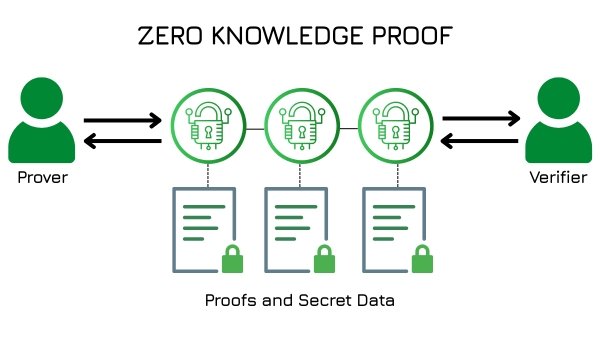
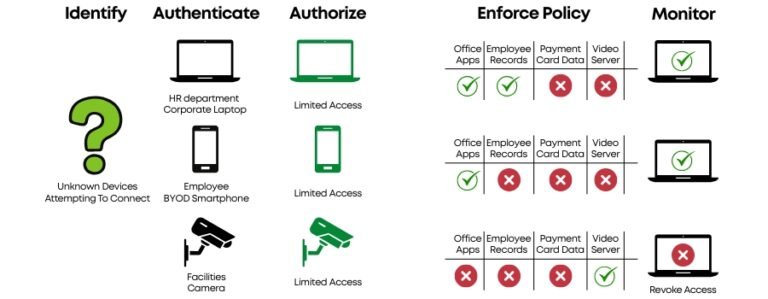
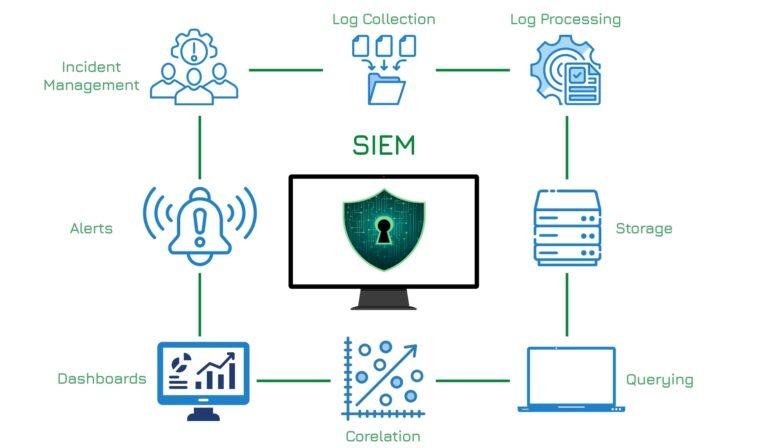
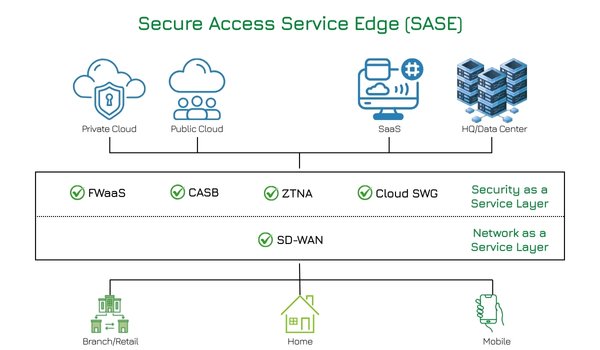
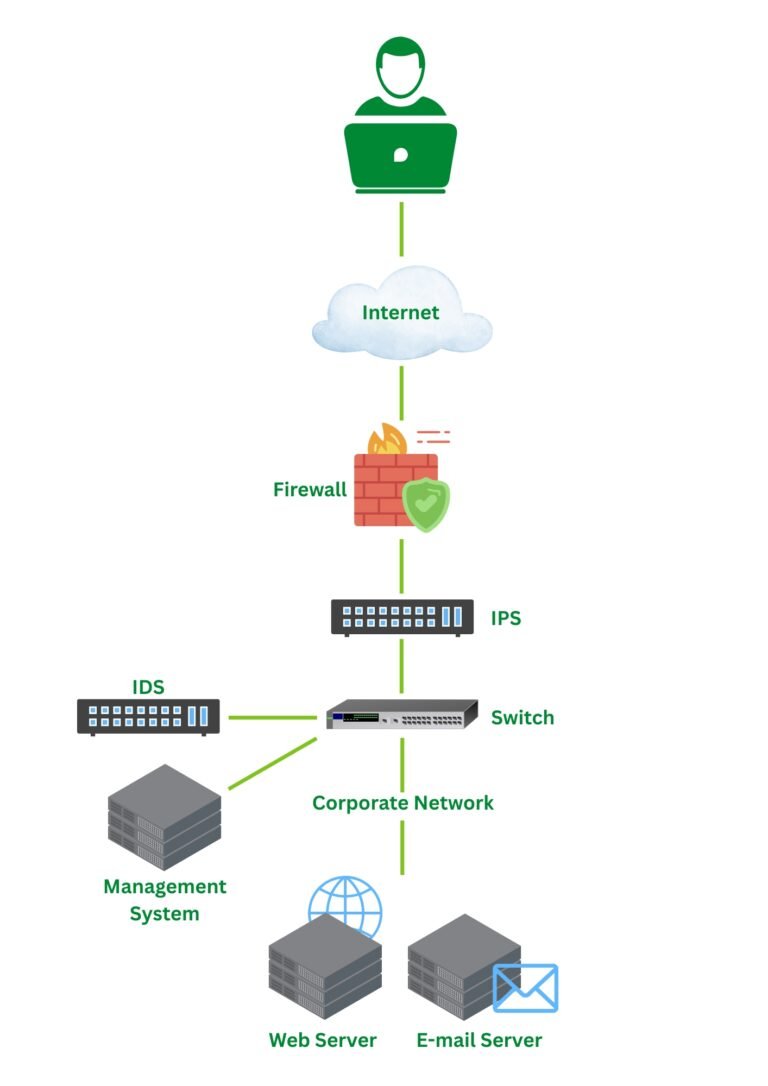
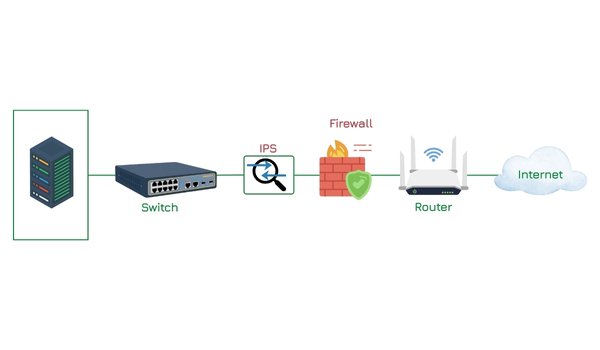
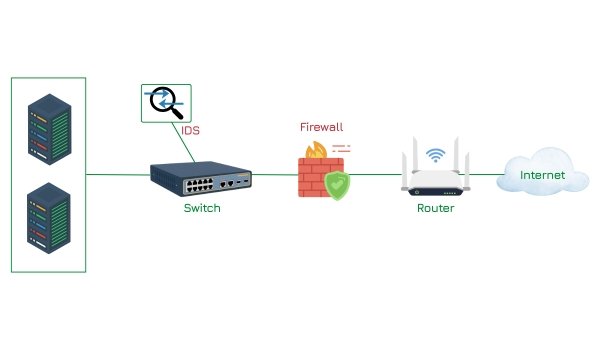
QSAN Nepal’s Sole Distributor: Insight Technology Powers Enterprise Storage Revolution
QSAN Technology delivers enterprise-grade storage solutions specializing in high-performance Network Attached Storage (NAS), Storage Area Networks (SAN), Direct Attached Storage (DAS), and unified NVMe arrays for data protection and management. It is optimized for demanding data centers featuring cutting-edge NVMe flash arrays, unified block/file/object storage, and container-ready compute nodes with dual-controller redundancy for zero-downtime operations.Continue reading "QSAN Nepal’s Sole Distributor: Insight Technology Powers Enterprise Storage Revolution"