
Network Access Control Provides Visibility · Real-time Control · Orchestration . Know and Control what’s on your networks and provide Guest Portal to BYOD .
What is Network Access Control ( NAC ) ?
NAC ( Network Access Control ) is a security measure to obtain visibility of devices inside your network and enforcing policy to objects and users to manage access in your corporate networks. NAC provides various use cases and typical customer requirements. Few of the Uses cases are:
- Plug and Protect
- Visibility – Agent less
- Zero trust protection
- Compliance and control
- Orchestration and Zero day
- Guest Device Registration
What is Agent ?
An agent is a code that might perform any functionality based on Software or Application residing somewhere in different places. Persistent, Dissolving and Agent less solution are different agent solutions in NAC implementation.
Persistent Agent -> These type of agent reside in the device of the user that are trying to get into your network or domain
Dissolving Agent -> These Agents simply reside in any web or hyperlink and once a user want to get into your network or domain it gets downloaded in the users device. Once the Task of the Agent accomplished it gets dissolve from the users devices.
Agentless -> These are integrated with third party solutions like AD, EPP, Path and Anti-Virus.
After talking about the agents and agentless solutions lets get into Agentless NAC implementation and few Use Cases:
Device Discovery and Device Classification
- Device Detection and Profiling:
Any Device that want to get into your domain will first be Discovered using any of the broadcast messages such as DHCP discover, ARP Broadcast. After which Active Profiling ( NAMP or other scanning services ) and passive profiling ( Comparison of DHCP fingerprint records ) will try to profile your devices on the basis of following categories
i. Operating System
ii. Access Group
iii. New Devices
iv. Device by Subnet
v. By Flag
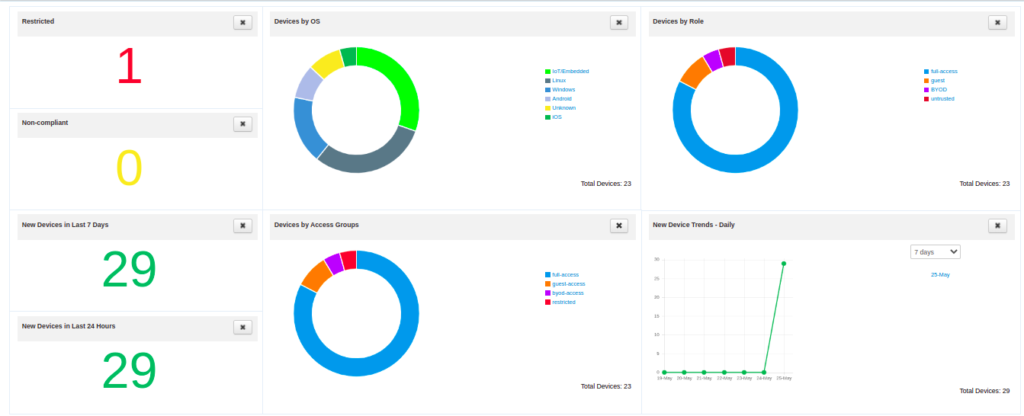
2. Device Classification:
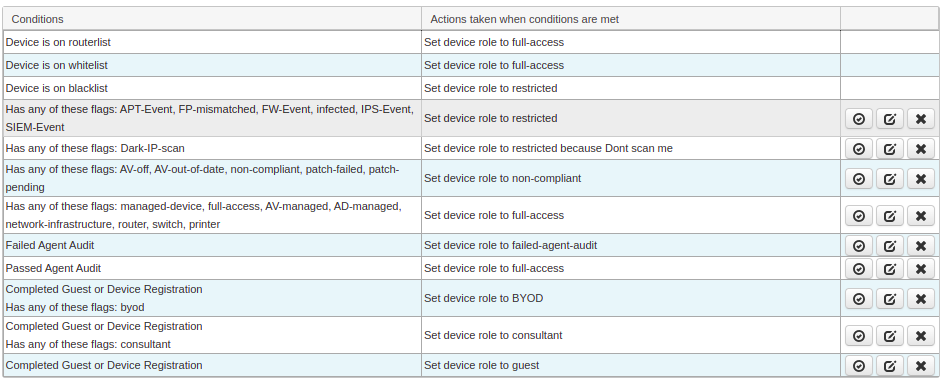
After Network Access Control ( NAC ) discovers a new Device or endpoint joined in the network, It determine those endpoints role by using Automated Device Classification Policy. Once any endpoint matches with the policy on Automated Device classification policy it will be assigned the role accordingly and if non of the policy matches the device will be assigned the role as untrusted.
How does NAC Restrict the Unauthorized user using ARP Enforcement ?
The Device create a Rouge ARP table so that the unauthorized and untrusted devices doesn’t communicate with other trusted device. For this to accomplish , when a device is categorized as untrusted or restricted devices the Network Access Control (NAC) continuously ARP reply the host that is untrusted so that the ARP table of the restricted devices changes to the NAC appliance. Because of this rouge ARP table the traffic from these unauthorized device is now diverted to pass through NAC.
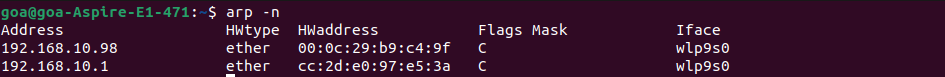
ARP table before the device is Considered untrusted and restricted.
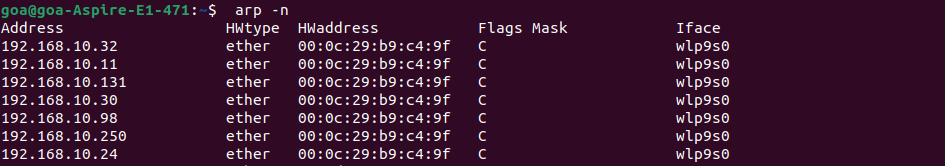
ARP table after the device is Considered untrusted and restricted
BYOD and Guest Portal
Nowadays BYOD policies are existing everywhere, due to this the devices that connects to your network/domain may contain various malware , or patches problem that are not detected by firewall so for these devices we can set up ACL in Network Access Control ( NAC ) to redirect your BYOD device to an HTTP captive portal.In the Captive portal, guest register themselves and sponsors can Manage those devices .
These Devices Can be provided with access with mail, whatsapp from sponsors or web interface of NAC.
Guest Management using Email Service
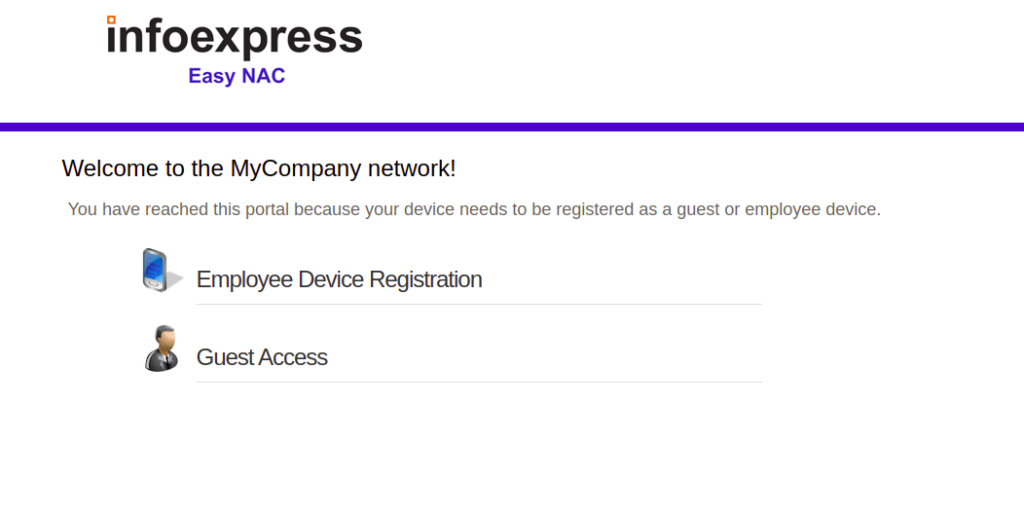
After users are redirected to Guest Portal they can either complete the guest authentication using Employee Device Registration which can be integrated with AD or by completing the Guess Access Form fillup.
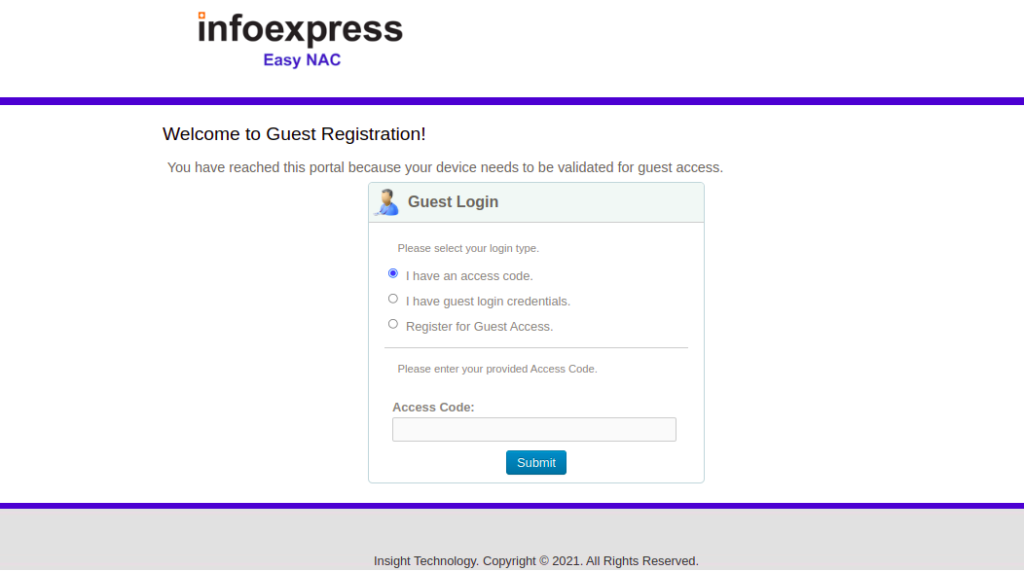
Guest can either complete the authentication using pre-generated access code from the sponsors or by filling up the Guest Registration Form
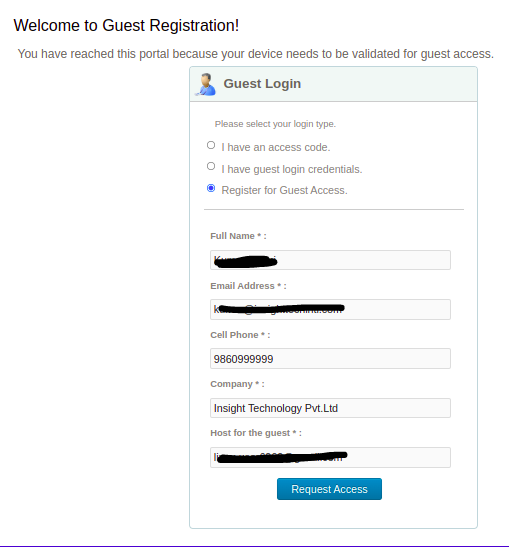
After submitting the request, guest will be redirected to a new page with guest’s details and the sponsor will get mails so that they can accept or reject the request.
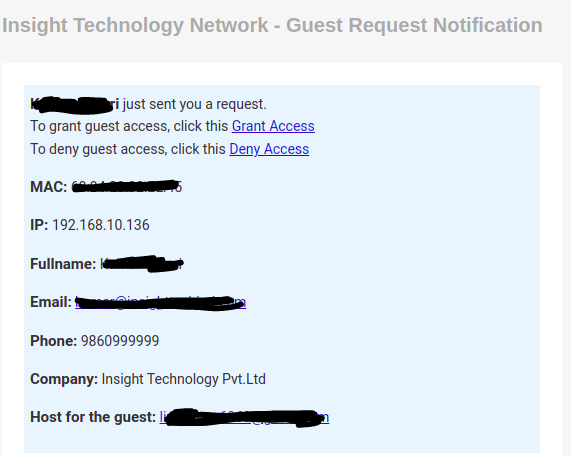
The host will get the email as above mentioned and can accept or deny the request not only from within the network but from outside the network too with the use of various keywords.
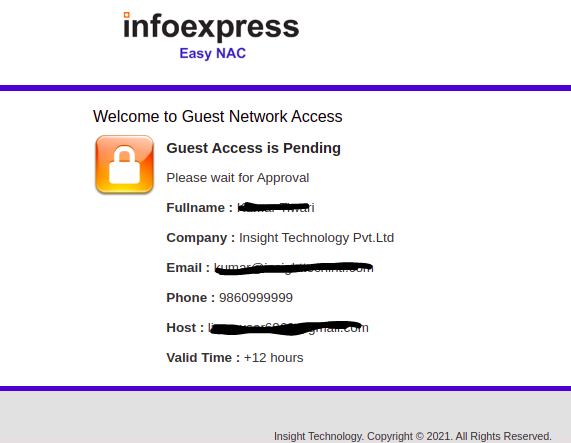
Until and unless the guest are not grant access they will receive a pending message in the portal and will not be able to authenticate or get into any parts of the network which will be decided in accordance to the ACL created.
Do NAC perform all the operation performed by Firewall, End Point security and other security infrastructure ?
In the subject of networking, several devices fulfill a variety of roles. As previously said, firewalls are used to manage various incoming and outgoing traffic, antivirus software is used to detect viruses with recognizable signatures, and SIEM is used to centralize logs and do various analyses. NAC can inherit some of these security infrastructure’s features, but it can’t totally replace them. What NAC does is integrate these devices within itself so that any modifications or behavior detection are collected, and devices with those behaviors are assigned various responsibilities and ACLs as appropriate.
For example :
i. Various security infrastructure, such as SIEM, may record logs and perform some manual tasks for a device that is constantly scanning your networks for known IP and open ports, but with NAC, once this is detected, the devices that are performing these attacks are assigned the role of Dark-Scan-IP and are restricted to a captive portal where the user must register himself as an employee for testing or as a guest with those tasks as needed.
ii. The goal of an antivirus server is to identify malware and quarantine those files . However, with the addition of NAC to the AV, these devices with identified viruses may be quarantined, preventing lateral network propagation.
With these in mind we can conclude that your current network may have an AV , Firewall or other security infrastructure but with NAC these devices will be integrated to remedy various loop holes arising due to these device working in isolation and provide your network with all known various features to protect and restrict unauthorized access on the basis of user and provide complete visibility. Also users with restricted, unauthorized access, BYOD devices will be redirected to Captive portal so that only those who need to be in network are provided with the access either through web, email or whatsapp integration.

