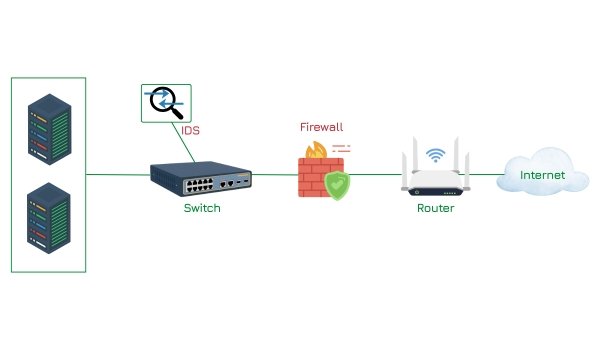
A security technology that acts as an early warning system by detecting potential threats, unauthorized access, or malicious activities and alerting administrators for timely action. I
What is Intrusion Detection System (IDS) ?
An Intrusion Detection System (IDS) is a network security tool that monitors network traffic and devices for suspicious activity and policy violations or any kind of unauthorized access attempts. When the anomalies or known threats are detected then it generates alerts for administrators, enabling rapid investigation and response, but does not actively block traffic.
Classification of Intrusion Detection System (IDS)
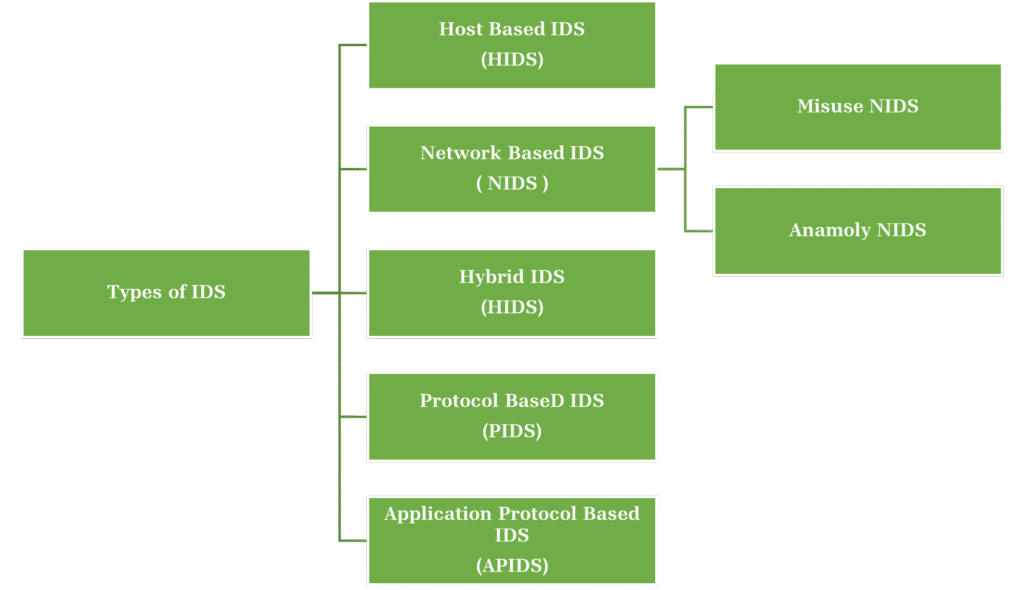
- Host Intrusion Detection System (HIDS)
- It is installed on individual devices which monitors inbound and outbound packets and system files for malicious behavior.
- Network Intrusion Detection System (NIDS)
- It monitors and analyzes traffic across an entire network segment to detect suspicious activity.
- Hybrid Intrusion Detection System
- This combines multiple IDS types (HIDS and NIDS) for comprehensive network and host-level monitoring, improving detection accuracy.
- Protocol-based Intrusion Detection System (PIDS)
- It focuses on monitoring and analyzing protocol activity between users and servers, primarily on web serversIt tracks connection protocols such as HTTP, HTTPS.
- Application Protocol-based Intrusion Detection System (APIDS)
- It monitors application-specific protocols within servers to detect attacks targeting application communication.
FIREWALL VS IDS VS IPS
IDS works in conjunction with firewalls and IPS where 3 of them forms a complementary layers of network defense.
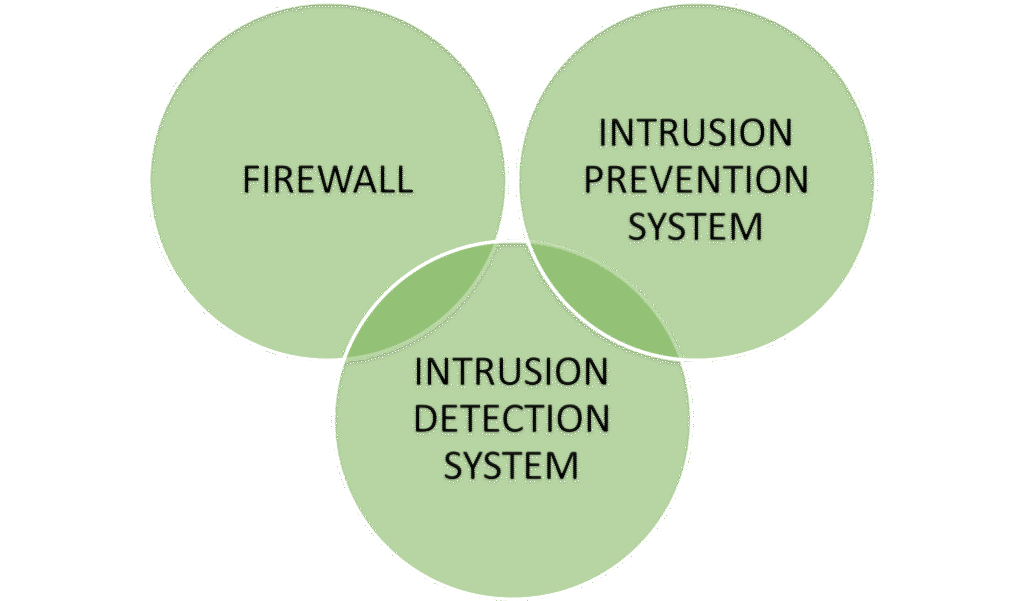
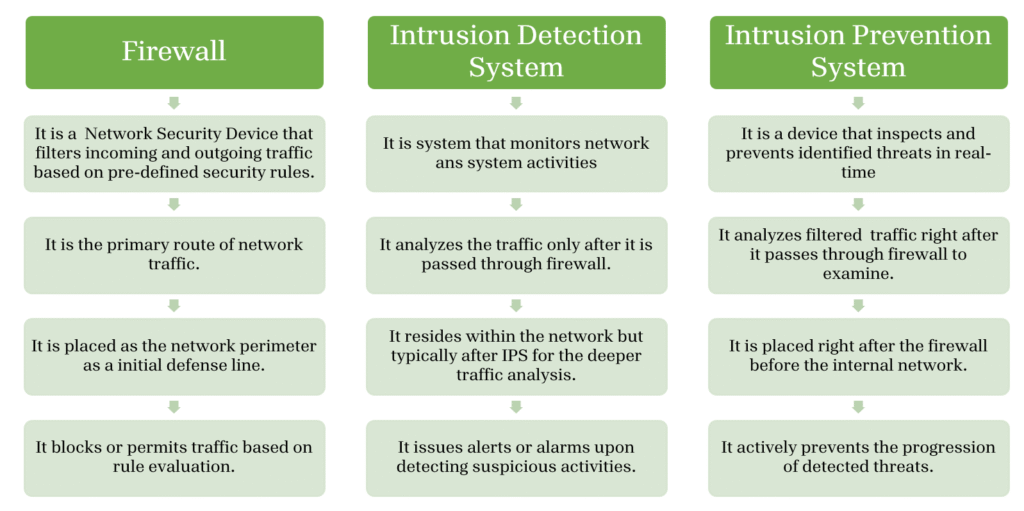
Hence ,this integration of Firewall, IDS and IPS ensures faster threat detection, automated response, reduced risk of breaches, and improved overall security posture, making networks resilient against evolving cyberattacks. Combining these technologies delivers a balanced approach where prevention, detection, and control reinforce each other for optimal defense.
INTRUSION DETECTION METHODS
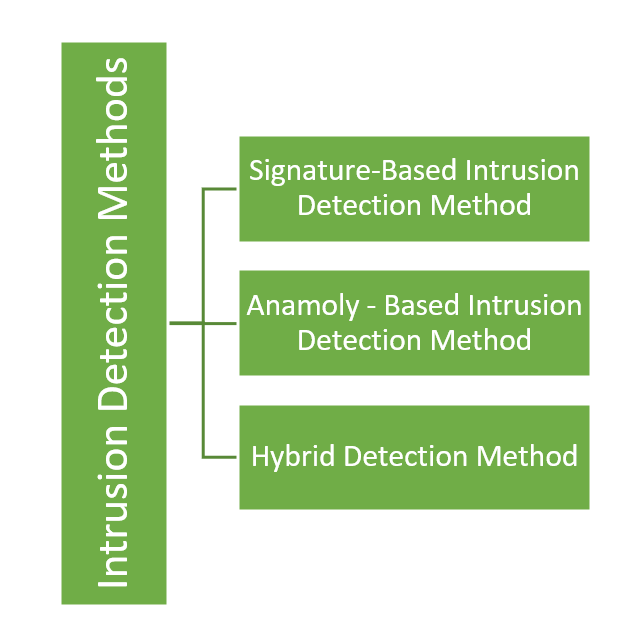
- Signature-Based Detection
- Uses a database of known attack patterns to identify threats with high accuracy but cannot detect new, unknown attacks.
- Anomaly-Based Detection
- Establishes a baseline of normal activity and flags deviations as potential threats, capable of detecting new or zero-day attacks.
- Hybrid Detection
- Combines both signature and anomaly detection methods for comprehensive threat identification, leveraging the strengths of each
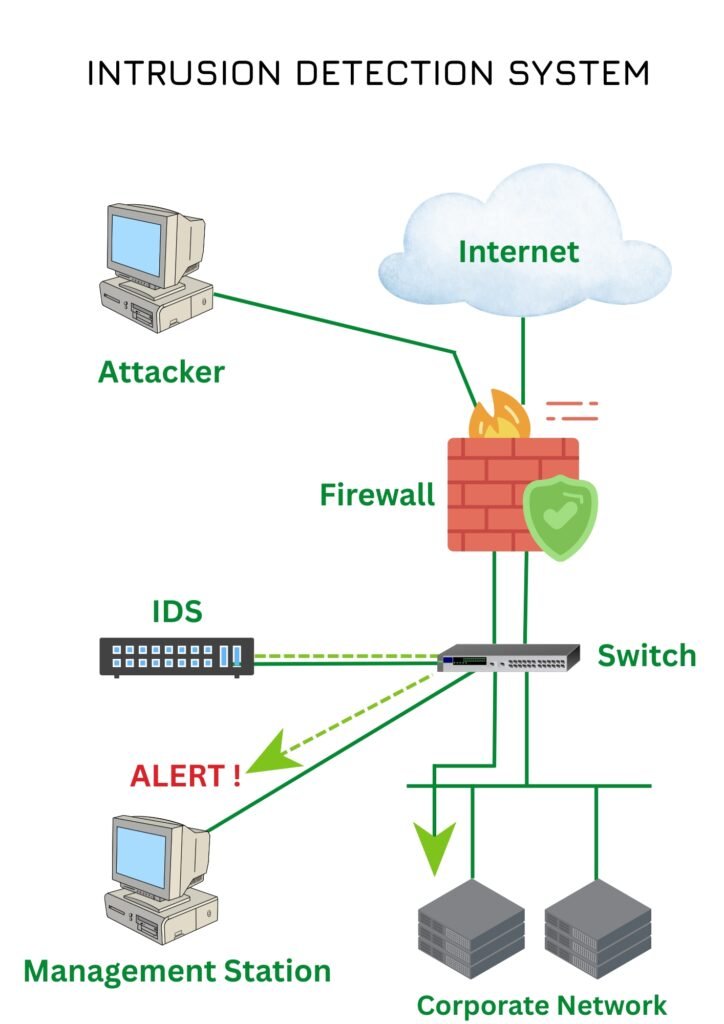
WORKING MECHANISM OF INTRUSION DETECTION SYSTEM
- An IDS continuously monitors network traffic to detect any suspicious or abnormal activity.
- It analyzes the data flowing through the network, looking for patterns and signs of potential threats.
- The system compares observed network activity against a predefined set of rules and known attack signatures.
- When a match or anomaly is detected, the IDS generates an alert.
- The alert is sent to the system administrator or security team for investigation.
- Upon receiving the alert, the administrator examines the activity to determine if it is a genuine threat.
- Necessary actions are then taken to prevent damage or stop further intrusion.
- Hence in such way, IDS helps in early detection of threats, facilitating faster response and minimizing potential harm to the organization.
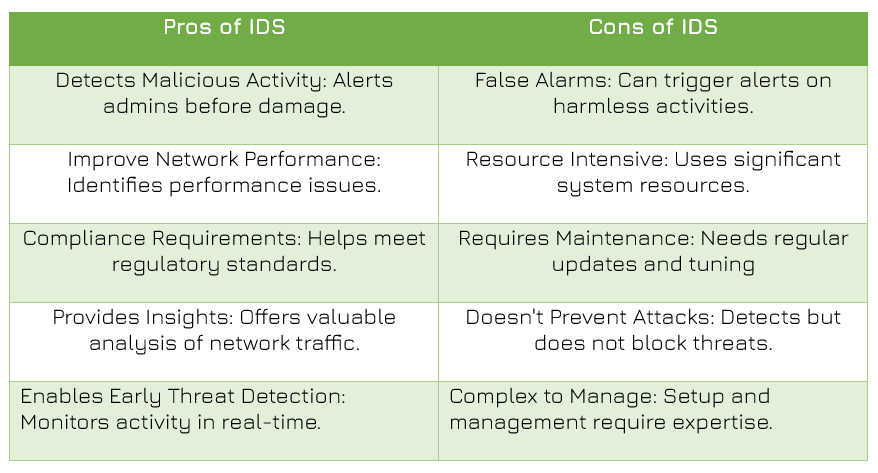
ADVANTAGES/DISADVANTAGES
CONCLUSION
In conclusion, an Intrusion Detection System (IDS) is a crucial component in modern cybersecurity, offering continuous monitoring and early detection of suspicious activities to prevent potential breaches. IDS provides valuable insights into network traffic, improving incident response and overall security posture. At Insight Technology, we provide advanced IDS services designed to empower organizations with real-time threat detection, detailed network visibility, and compliance support. Our IDS solutions help businesses proactively identify and mitigate risks, ensuring robust protection and operational continuity in an increasingly complex threat landscape.This trusted, end-to-end approach makes Insight Technology the preferred partner for effective and resilient network defense.

