
Endpoints is referred to as any kind of device ranging from laptops and smartphones to IoT devices that connect within a network system. These often serve as the initial entry points for attackers. So the process of securing such end points against cyberattacks is known as Endpoint Security.
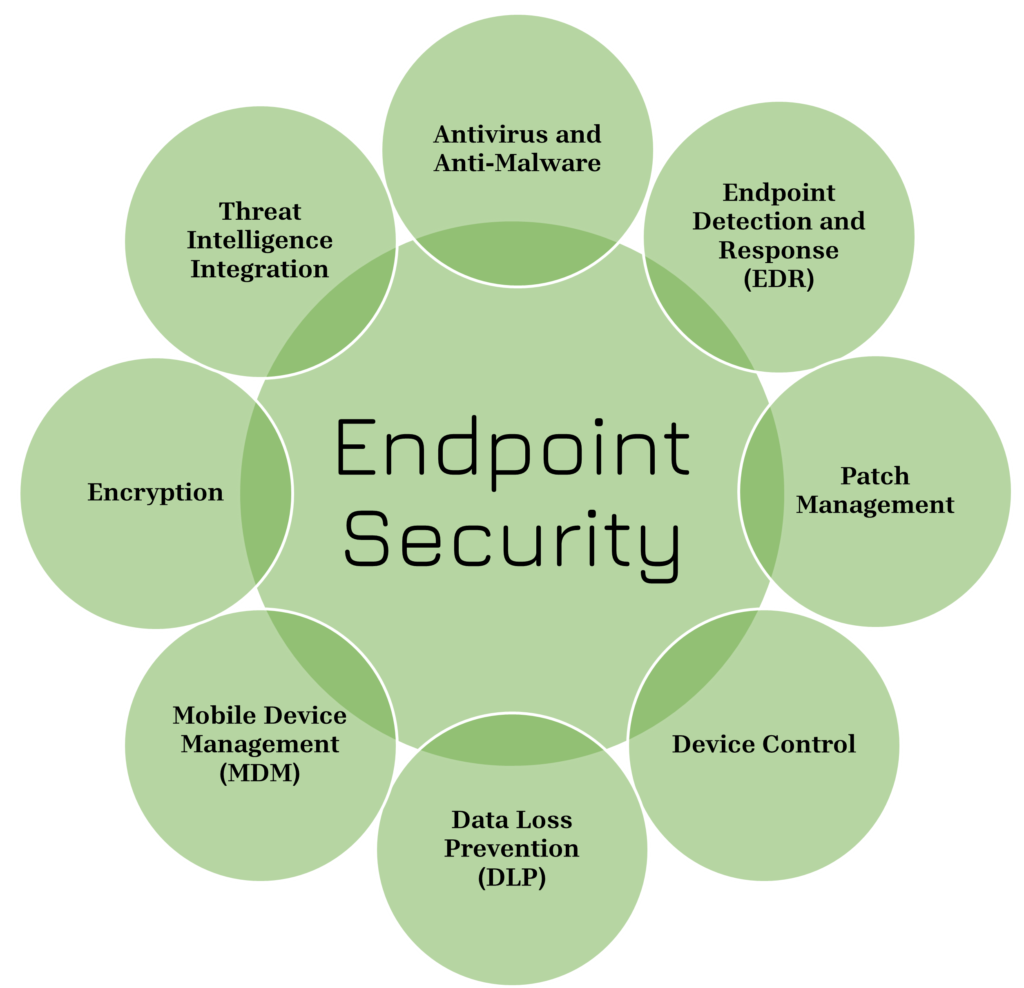
Core Components of Endpoint Security
A Quick Glance at Endpoint Security in Nepal
Nepal’s endpoint security market is rapidly expanding, driven by the country’s accelerating digital transformation and a rising tide of cyber threats targeting endpoints such as laptops, mobile devices, and servers. Market forecasts estimate endpoint security revenue in Nepal to exceed USD 2.7 million in 2025, with a strong annual growth rate of over 14% expected through 2030. This growth is fueled by increasing adoption of remote work, cloud technologies, and digitization in industries like banking, healthcare, and government sectors. Leading cybersecurity players in Nepal, including Insight Technology Pvt. Ltd., are meeting demand with advanced endpoint solutions integrating AI-powered threat detection, automated incident response, real-time monitoring, and data loss prevention, helping enterprises reduce attack surfaces and ensure regulatory compliance amidst evolving risks. Endpoint security forms a critical layer of Nepal’s broader cybersecurity ecosystem, enabling safer digital operations in an increasingly connected world.
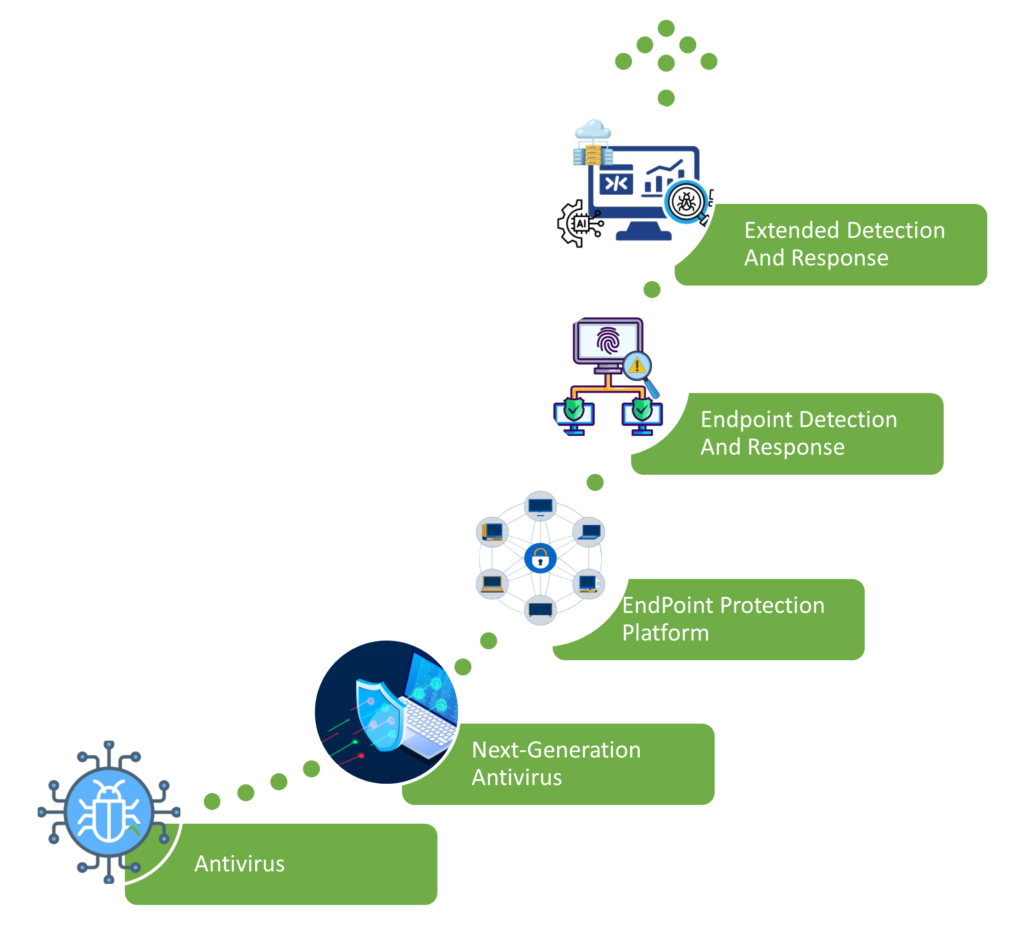
Evolution of Endpoint Protection
Endpoint security evolved through these layered technologies, each building on the last to counter sophisticated threats.
Antivirus (Traditional AV)
Signature-based scanning for known malware; reactive, file-focused protection requiring manual updates—effective against basic viruses but blind to zero-days.
Next-Generation Antivirus (NGAV)
Adds behavioral analysis, ML/AI, and cloud intelligence to block fileless attacks, exploits, and unknowns pre-execution; proactive with minimal performance hit.
Endpoint Protection Platform (EPP)
Comprehensive prevention suite combining NGAV, firewalls, app controls, and encryption; enterprise-scale policy enforcement via centralized consoles.
Endpoint Detection and Response (EDR)
Real-time telemetry collection for threat hunting; detects advanced persistent threats with isolation, forensics, and automated playbooks.
Extended Detection and Response (XDR)
Cross-domain correlation (endpoints + network + identity + cloud); AI-orchestrated response across the stack for unified visibility and faster MTTR
Key Components of Endpoint Security
- Endpoint Detection and Response (EDR) is a cybersecurity solution that continuously monitors, detects, investigates and responds endpoint threats.
- Patch Management is the process of routinely updating software, applications, and Operating systems with security patches that helps to mitigate vulnerabilities and ensures the resilience of end point security.
- Device Control is the process ofregulating and enforcing policies on devices connected to the network to prevent the data from malwares and unauthorized access.
- Data Loss Prevention (DLP) is a set of tools and policies that prevent the data from unauthorized personel and reduce the risk of it being lost, leaked, or accessed.
- Mobile Device Management (MDM) is the process of managing and securing mobile devices that are being accessed under corporate network and data.
- Encryption is the process of preventing unauthorized access of data and maintaing CIA Traid by encoding data at rest (files saved in hard drives, cloud storage), and data in transit (mesaage from sender to receiver).
- Threat Intelligence Integration is the process of combining threat data from external and internal sources that enhance threat detection and response stratergy.
Endpoints Lead the Risk Chart
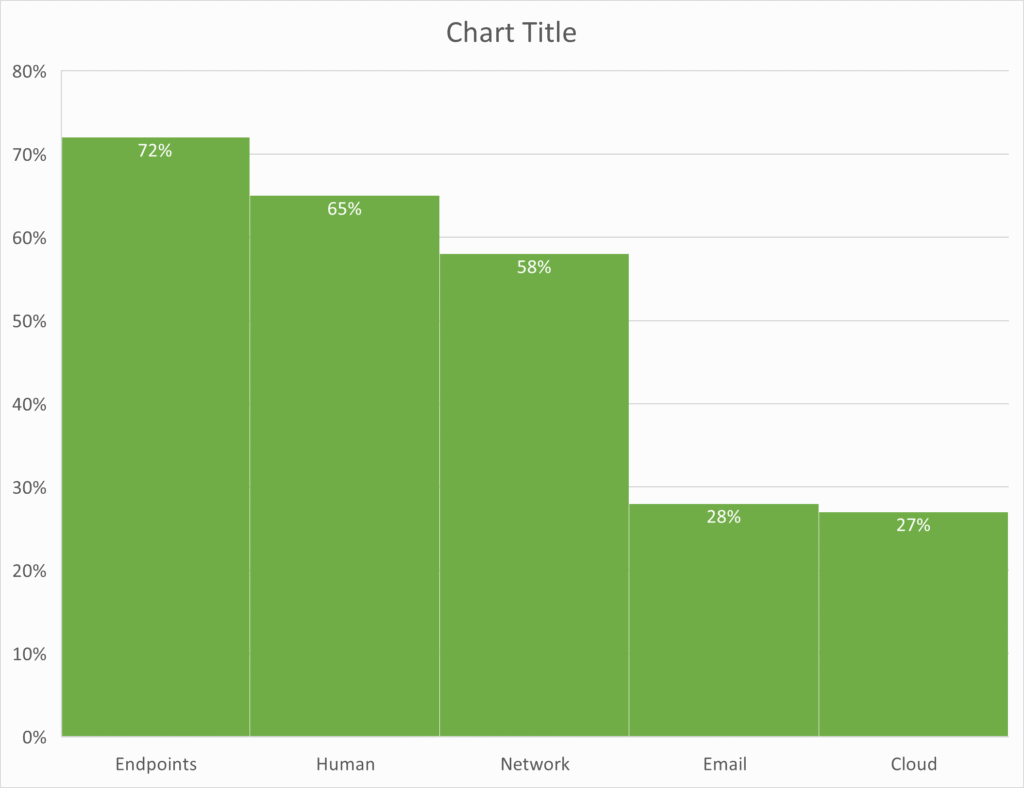
- Endpoints -72%
- The highest bar indicates that the majority of attacks or breaches start or involve endpoint devices (laptops, PCs, mobiles, servers), so they are the primary entry point that needs protection.
- Human-65%
- Shows the impact of human factors (phishing clicks, weak passwords, misconfigurations) as a major contributing cause of incidents.
- Network -58 %
- Represents attacks that exploit network-level weaknesses such as open ports, exposed services, or poor segmentation.
- Email – 28%
- Indicates the proportion of incidents that originate via email vectors like phishing and malicious attachments.
- Cloud – 27%
- Shows incidents tied to cloud resources (SaaS, IaaS misconfigurations, exposed credentials), which are growing but still charted lower than endpoints.
This chart highlights that endpoints are the single most targeted area in modern cyber attacks, making them the critical focus for any security strategy. It visually shows how often different attack surface, endpoints, humans, network, email, and clouds are involved in incidents, clearly placing endpoints at the top of the risk spectrum.
Importance of Endpoint Security
Endpoints are often targeted as entry points by attackers and can serve as bridges to compromise entire networks. Effective endpoint security reduces risk, prevents data breaches, supports compliance with regulations, and protects organizational assets and sensitive information.
WORKING MECHANISM OF ENDPOINT SECURITY
Endpoint security’s working mechanism is a seamless cycle of deployment, monitoring, and response that keeps devices secure.
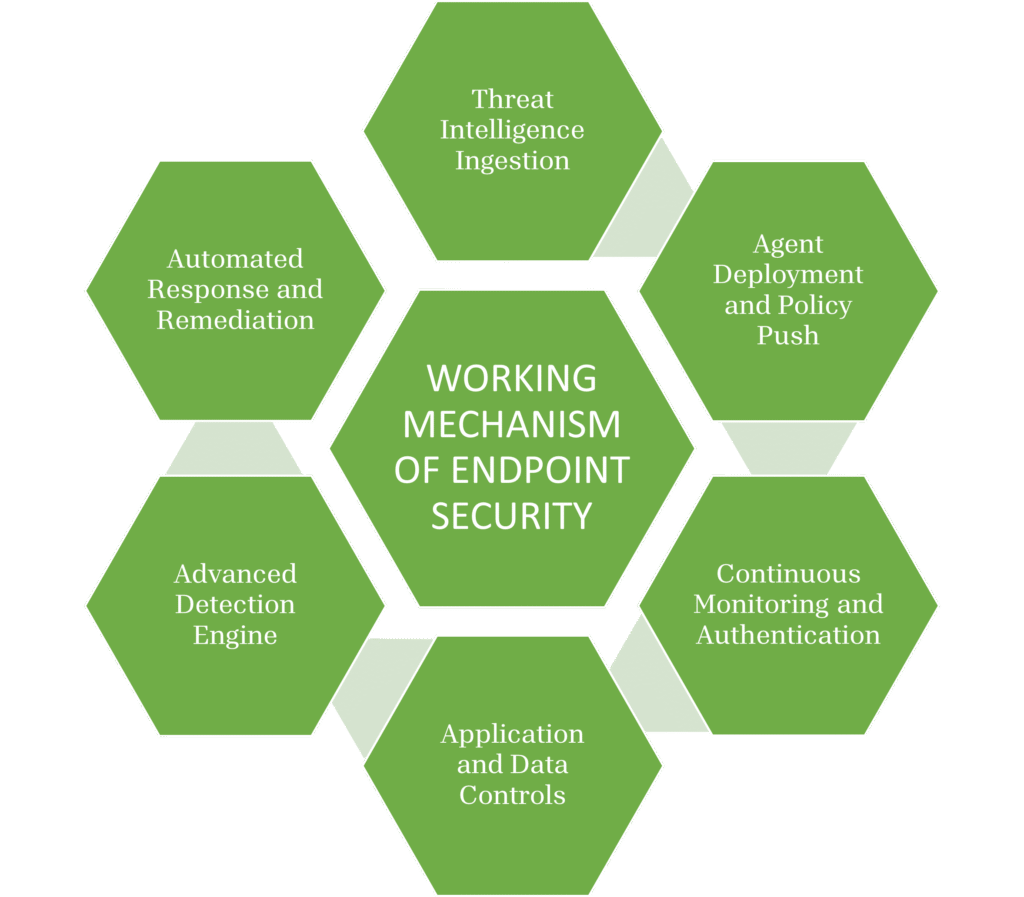
The working mechanism of endpoint security are as elaborated below :






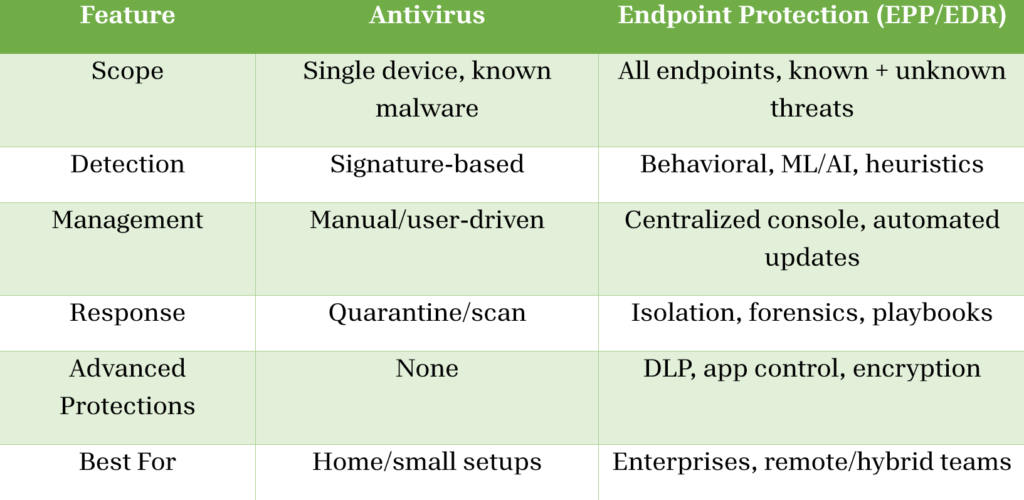
ENDPOINT SECURITY VS ANTIVIRUS
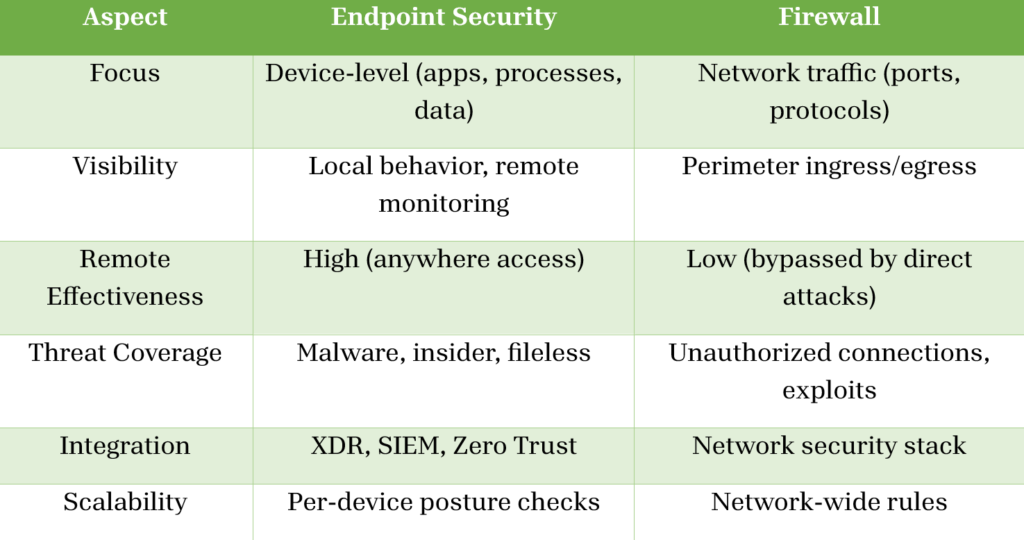
ENDPOINT SECURITY VS FIREWALL
In summary, endpoint security is a multi-layered approach combining prevention, detection, response, and intelligence, essential for safeguarding the expanding array of devices in modern interconnected environments

