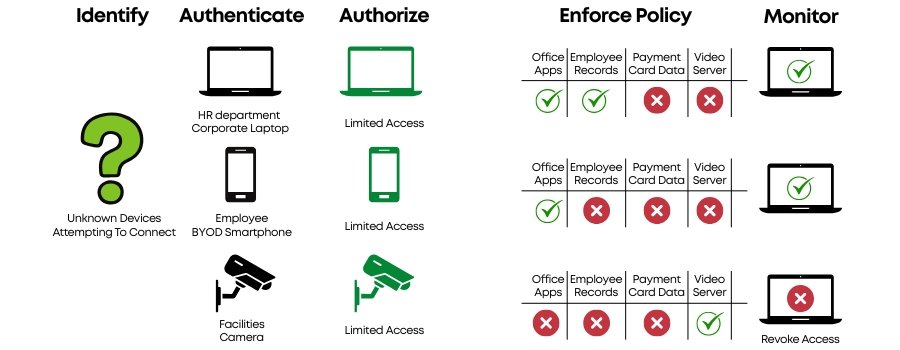
Network Access Control (NAC) is a comprehensive framework which ensures that only authenticated and authorized users and devices that comply with predefined security policies can connect to and interact with network resources. systems authenticate users, evaluate device compliance, and restrict access for unauthorized or non-compliant devices, reducing internal threats and ensuring access to only trusted devices.
CLASSIFICATION OF NAC
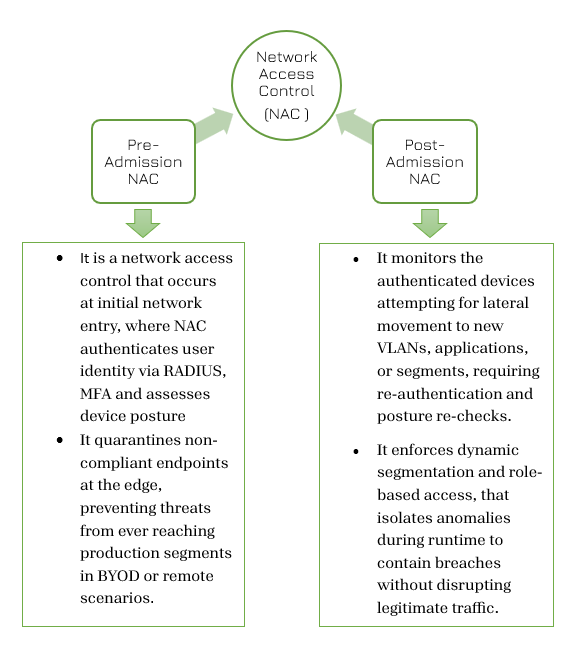
Inorder to maintain a secure network, NAC systems divide access management into diffrent phases as illustrated below:
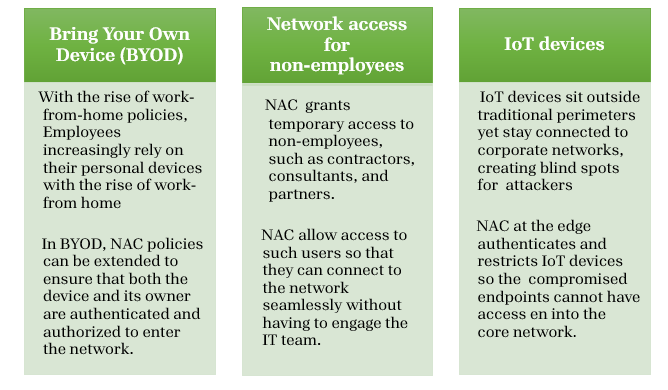
USE CASES OF NAC
Network Access Control (NAC) are designed to enforce security policies, control access, and maintain compliance across enterprise networks. Some of the key use cases where NAC provides significant value to organizations are :
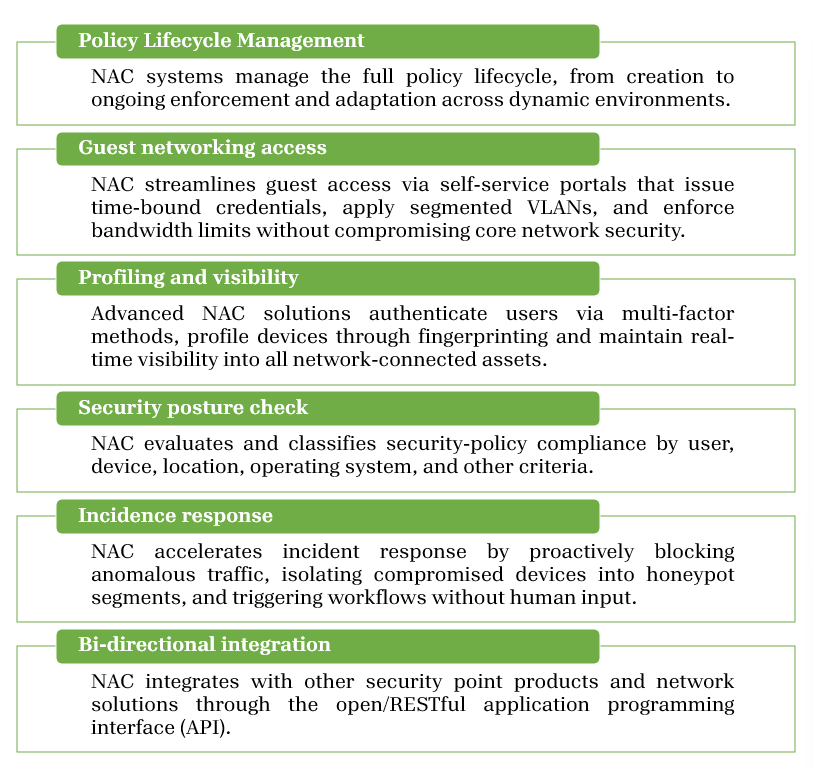
CAPABILITIES OF NAC
NAC plays an essential in securing enterprise networks by authenticating users and devices ,continuously enforcing policies and assessing security posture.The key capabilities of NAC helps to design a secure network environment, few of those capabilities are as listed below:
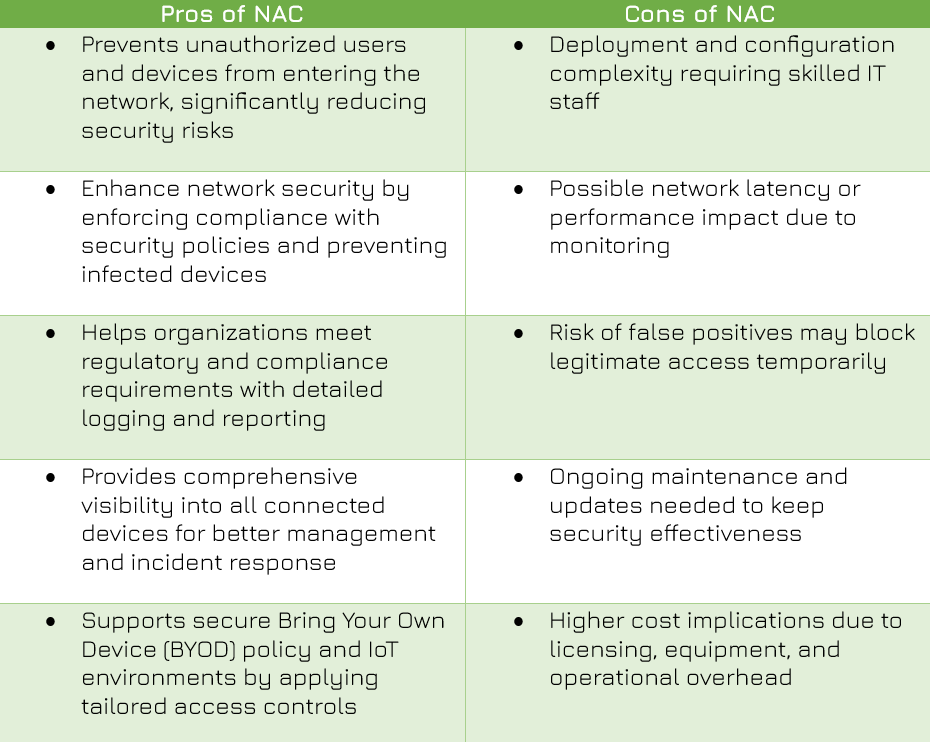
ADVANTAGES/DISADVANTAGES OF NAC
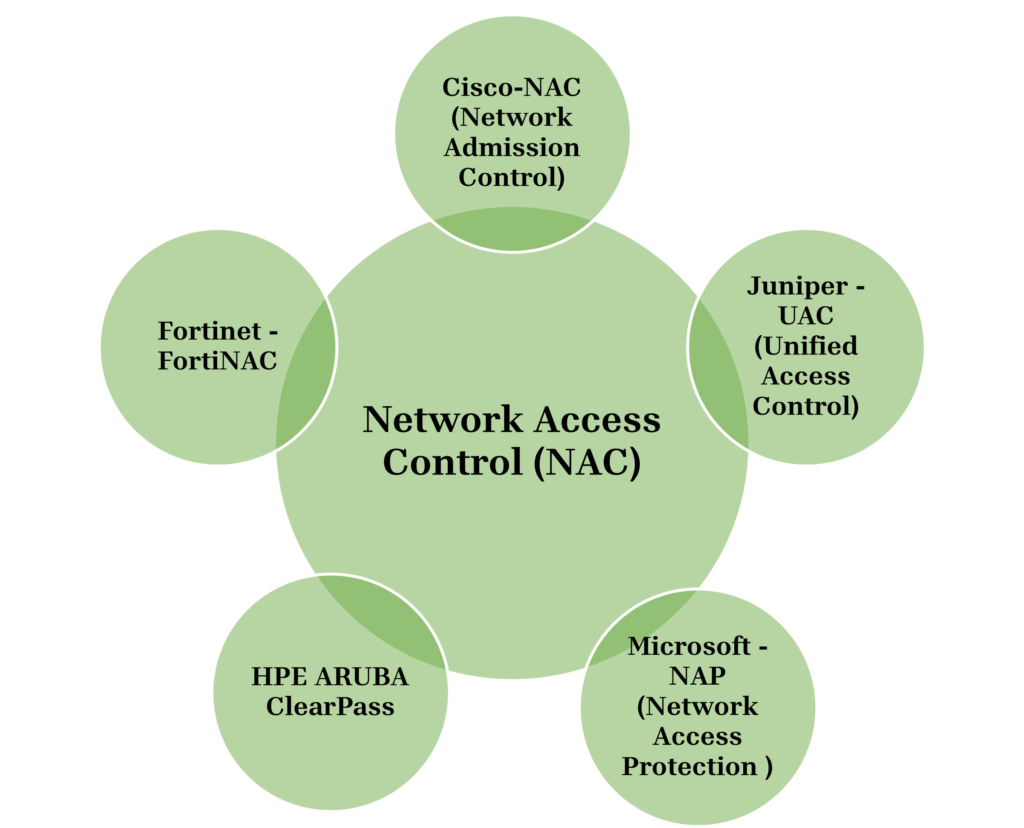
Naming Coventions of NAC Across Major Vendors
NAC solutions are critical for enforcing security policies and controlling access within modern enterprise networks. While each NAC vendor provides similar core functionality, their approach for naming conventions whether vary significantly.Few of the naming convention for NAC across multi-vendors are provided below:
CONCLUSION
Network Access Control (NAC) is an essential solution for modern enterprises, enabling secure, policy-driven access, continuous device monitoring, and protection against unauthorized users and threats. From pre-admission verification to post-admission enforcement, NAC ensures that networks remain compliant, efficient, and resilient. Insight Technology offers comprehensive NAC services in Nepal, helping organizations implement, manage, and optimize their NAC solutions to safeguard critical resources, streamline access management, and maintain a robust security posture in today’s dynamic digital environment.

