Intrusion Prevention Systems (IPS) emerged from the foundational work on intrusion detection in the mid-1980s , evolving from tools that simply alerted administrators to suspicious activity. Early systems combined rule-based and statistical methods to monitor network traffic for malicious behavior. Over time,the IPS has advanced by integrating automated preventive capabilities allowing them not only to detect but also to block threats in real time. This transition from reactive to proactive security has made IPS a critical component in modern cybersecurity, enabling organizations to guard against increasingly sophisticated attacks with speed and precision.
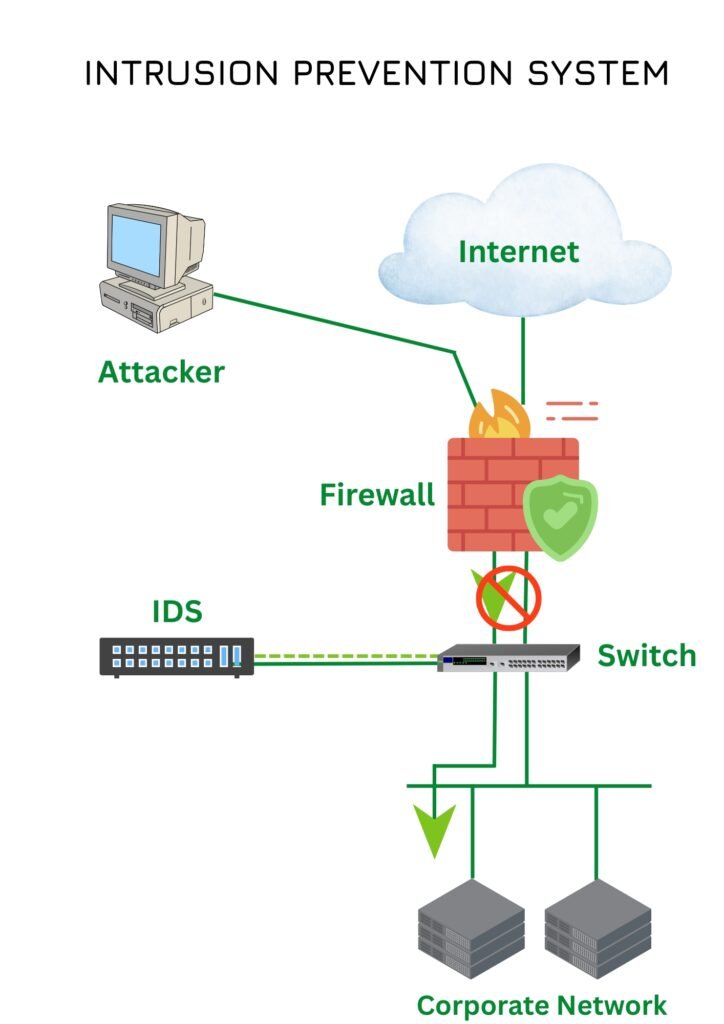
WHAT IS INTRUSION PREVENTION SYSTEM?
An Intrusion Prevention System (IPS) builds on IDS functionality that nort only detecting potentially malicious activity but also automatically takes action to block or prevent those threats from reaching their targets. IPS solutions often integrate real-time traffic analysis and signature-based threat detection, stopping attacks as they occur.
WHY IS IPS IMPORTANT ?
The organizations choose IPS technologies over traditional reactive network security efforts due as IPS standouts the best in the following ways
CLASSIFICATION OF INTRUSION PREVENTION SYSTEM
There are four noteworthy types of Intrusion Prevention System. They are as follows:
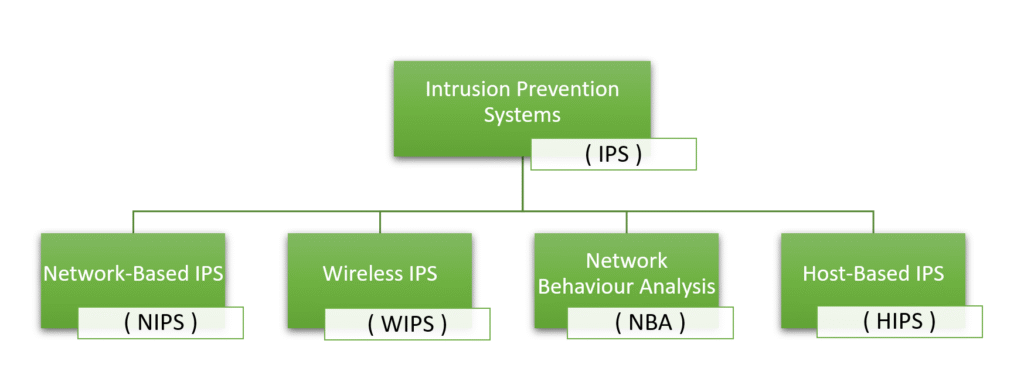
- Network-based IPS (NIPS)
- Monitors network traffic at strategic points to detect and block malicious activity across the entire network.
- Wireless IPS (WIPS)
- Focuses on wireless networks by detecting unauthorized access and blocking rogue devices.
- Network Behavior Analysis (NBA):
- Analyzes network traffic patterns to identify abnormal behaviors such as zero-day attacks or emerging malware.
- Host-based IPS (HIPS):
- Installed on individual devices, it monitors and prevents threats specific to that host by analyzing inbound and outbound traffic.
.
What Methods are used by Intrusion Prevention Systems?
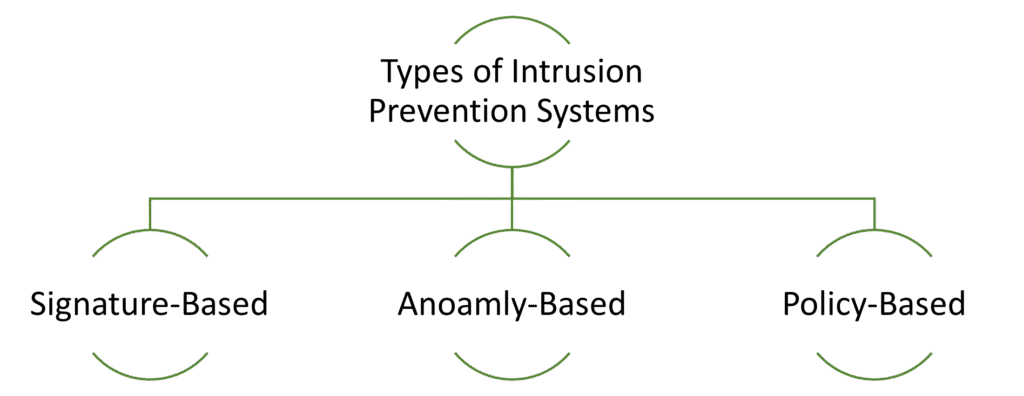
- Signature-Based Prevention
- Detects known threats by matching traffic against a database of attack signatures.
- Anomaly-Based Prevention
- Identifies deviations from normal behavior to detect unknown or new threats.
- Policy-Based Prevention
- Uses predefined security policies to block unauthorized or suspicious activities.
DETECTION METHODS USED BY IPS
Intrusion prevention systems perform more complex observation and analysis by the help of different detection mechansim few of them are as listed below:
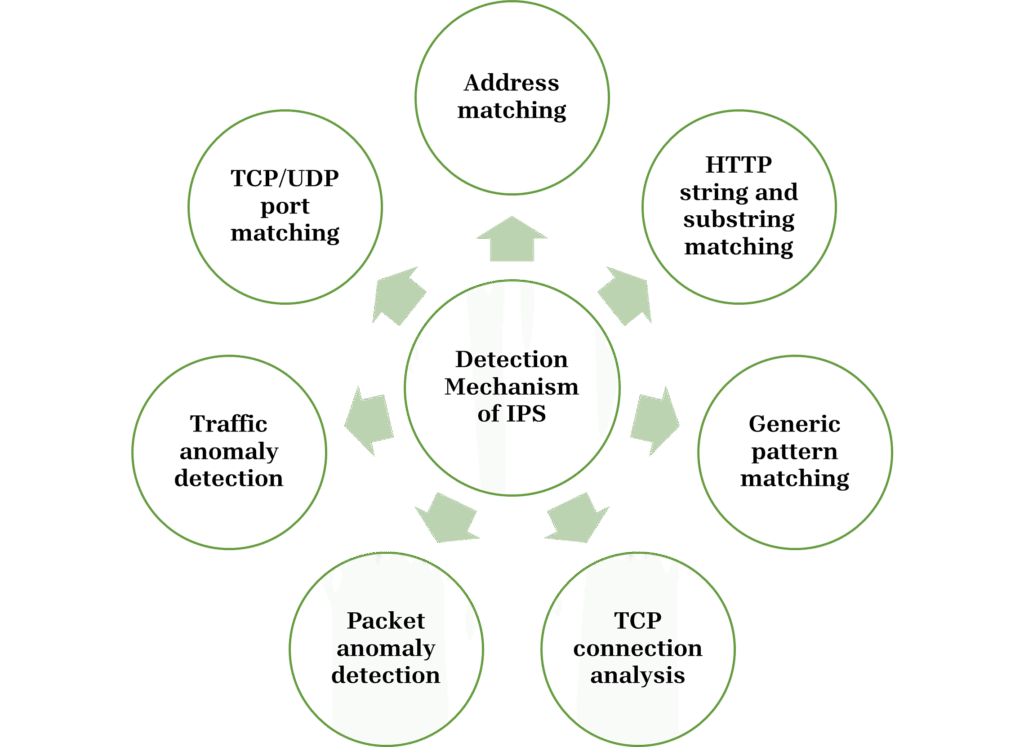
The different detection methods used by IPS are as explored below:
Address matching

HTTP string and substring matching

Generic pattern matching

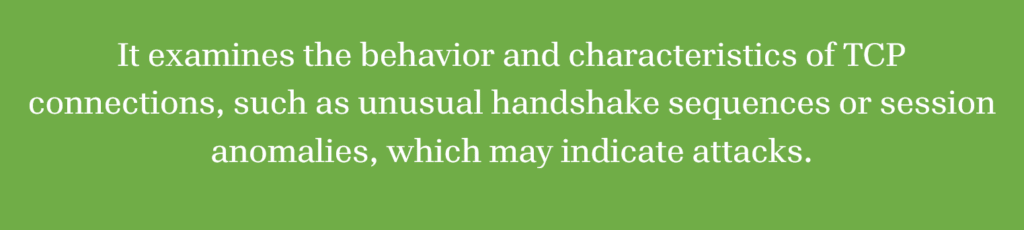
TCP connection analysis
Traffic anomaly detection

TCP/UDP port matching

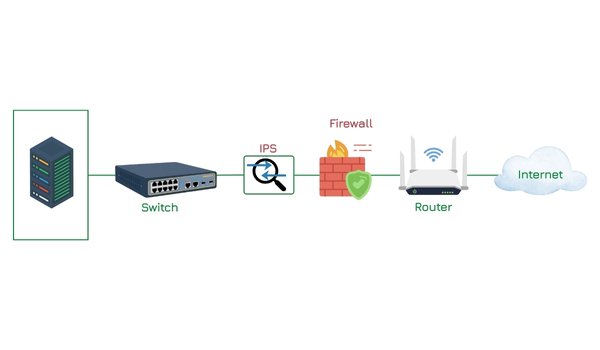
HOW DOES IPS WORK ?
The IPS follows an proactive approach that helps to maintain network integrity and prevents damage before it impacts systems.Those approach are as followed:
- IPS is installed inline within the network traffic path, directly between the source and destination.
- This inline positioning enables IPS to actively monitor and analyze all incoming and outgoing traffic in real-time.
- Unlike an IDS which only monitors and alerts, IPS takes immediate automated actions to block or mitigate threats.
- Common actions performed by IPS include sending alerts to administrators, dropping malicious packets, and blocking traffic from suspicious source addresses.
- IPS can also reset connections suspected of carrying attacks to terminate unauthorized sessions.
- Additionally, IPS can dynamically update firewall rules to prevent similar future intrusions.
- Usually deployed just behind the firewall, IPS acts as a proactive defense that not only detects but also prevents attacks from reaching network resources.
- This reduces the time window for attackers to cause harm and strengthens overall network security posture.
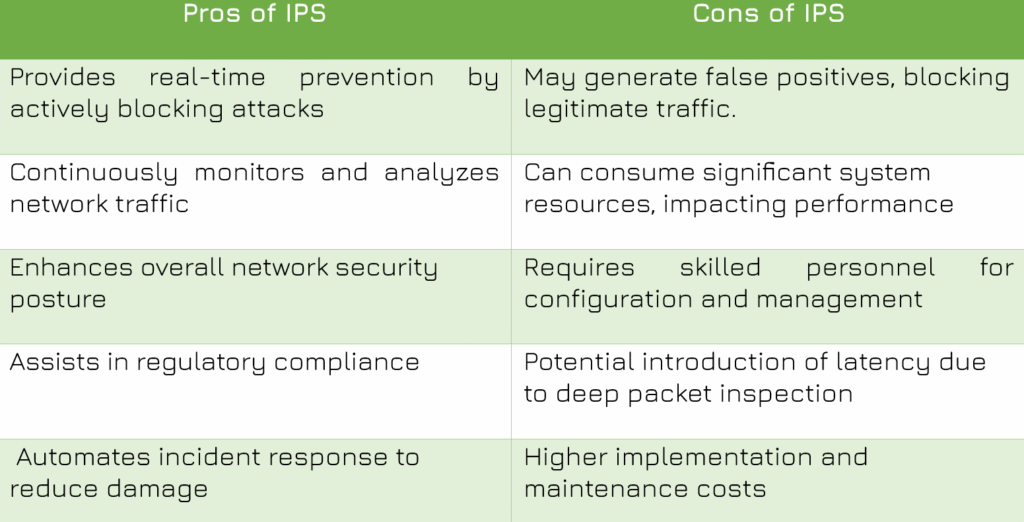
ADVANTAGES AND DISADVANTAGES OF IPS
CONCLUSION
In a nutshell, an Intrusion Prevention System (IPS) is a proactive security technology that continuously monitors network traffic to detect and block malicious activities in real time that protects organizations from malware, exploits, and unauthorized access. Insight Technology provides comprehensive IPS services that not only leverage advanced detection methods like signature-based scanning and anomaly detection but also deliver tailored, automated threat mitigation solutions. Choosing Insight Technology means benefiting from industry-leading expertise, innovative technologies, and a commitment to maintaining operational continuity. Our IPS services empower organizations to strengthen their network security posture, respond pro-actively to threats, and safeguard critical assets in today’s evolving cybersecurity landscape. This trusted, end-to-end approach makes Insight Technology the preferred partner for effective and resilient network defense.

