A Comprehensive Overview on Data Flow to Layered Attacks
OSI MODEL
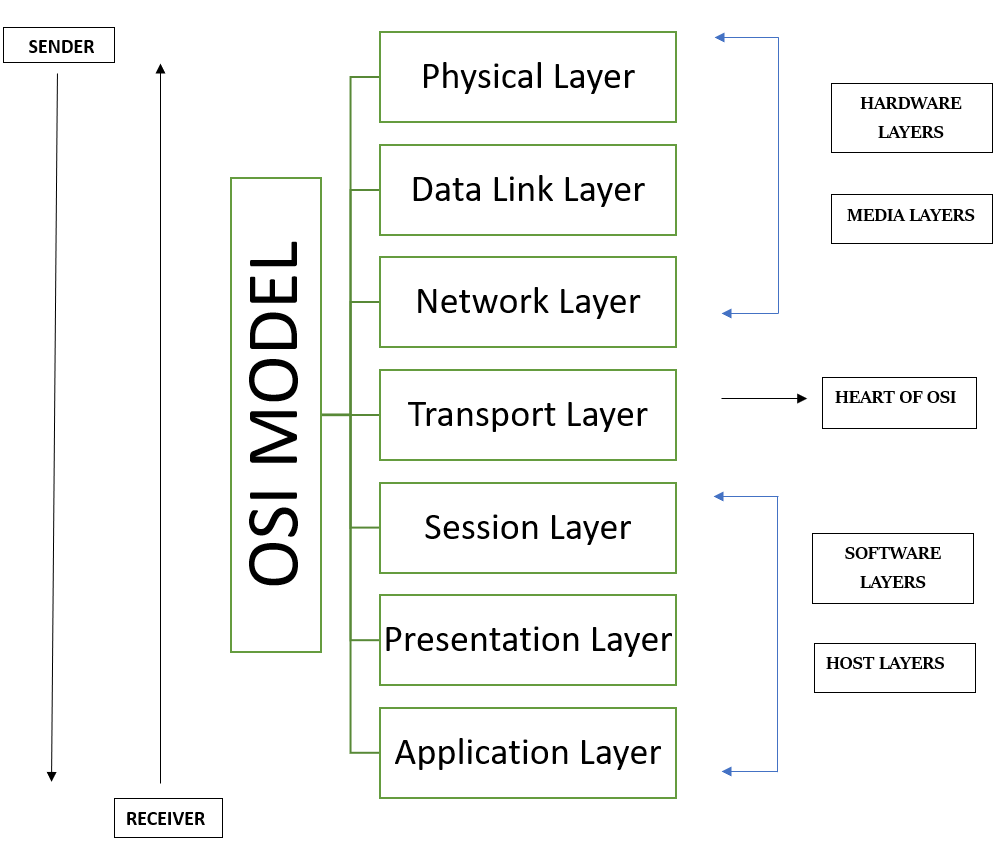
The OSI (Open Systems Interconnection) model is a conceptual framework that defines and standardizes how the computer systems communicate over the internet. Each layer in OSI Model has specific role in hadling data and each layer interacts with the other direclty.
It consists of 7 layers
The OSI model’s layered structure not only facilitates seamless communication across global IT supply chains but also shreads light upon specific vulnerabilities that are susceptible to targeted cyberattacks. In depth understanding of which OSI layers these attacks, it empowers and alerts organizations to deploy comprehensive, multi-layered defensive strategies ensuring secure, trustworthy international business communications.
This article provides an overview on OSI Model along with the attack vectors that target each layer, identifying each gap that attacker exploits.
target each layer, identifying each gap that attacker exploits.
Overview of 7 layers of OSI Model
Physical Layer
It is the bottom most layer of the OSI Model that concerns with transmitting raw bit stream over the physical medium such as cables, fiber, or wireless

This layer defines electrical and physical specifications for devices, manages how bits are encoded as signals, and establishes the connection between the physical devices. It acts as a groundframework for all higher-level communication that ensures the timing, bit synchronization, physical topologies, and transmission modes (simplex, half-duplex, or full-duplex) across network devices.
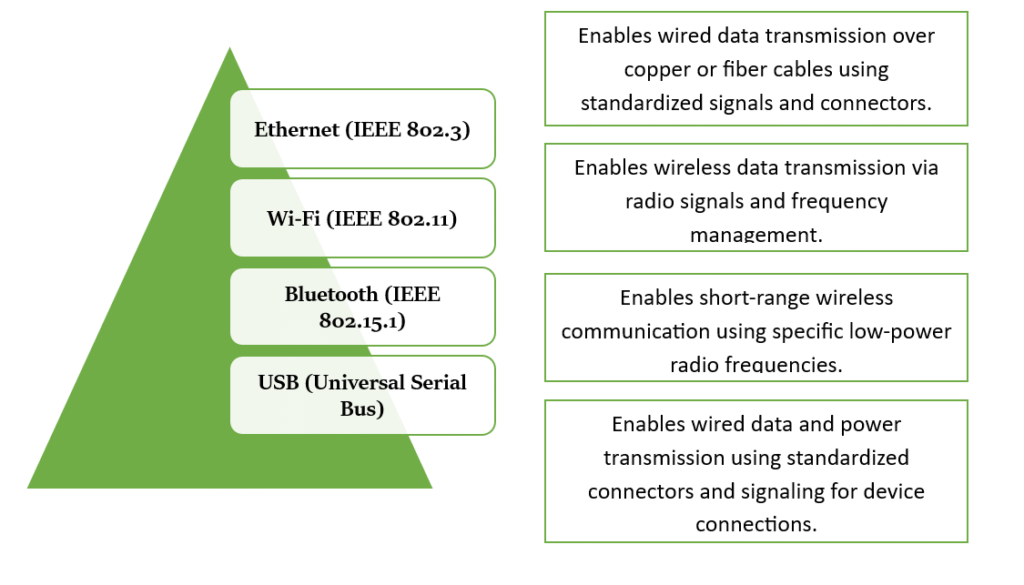
PROTOCOLS IN PHYSCIAL LAYER
Data Link Layer
It is the second layer of OSI model that is responsible for error-free node -to – node transmisson of data within the same network.This layer encodes , decodes and organize the incoming and outgoing data .
It converts packets from the network layer into frames, handles error detection and correction, manages flow control, and uses MAC addresses for device identification. This layer is divided into two sublayers: Logical Link Control (LLC) for flow/error management, and Media Access Control (MAC) for addressing and controlling access to the physical transmission medium.The switches, NICs, and bridges are the key devices operating at this layer that ensures secure and organized data transfer.
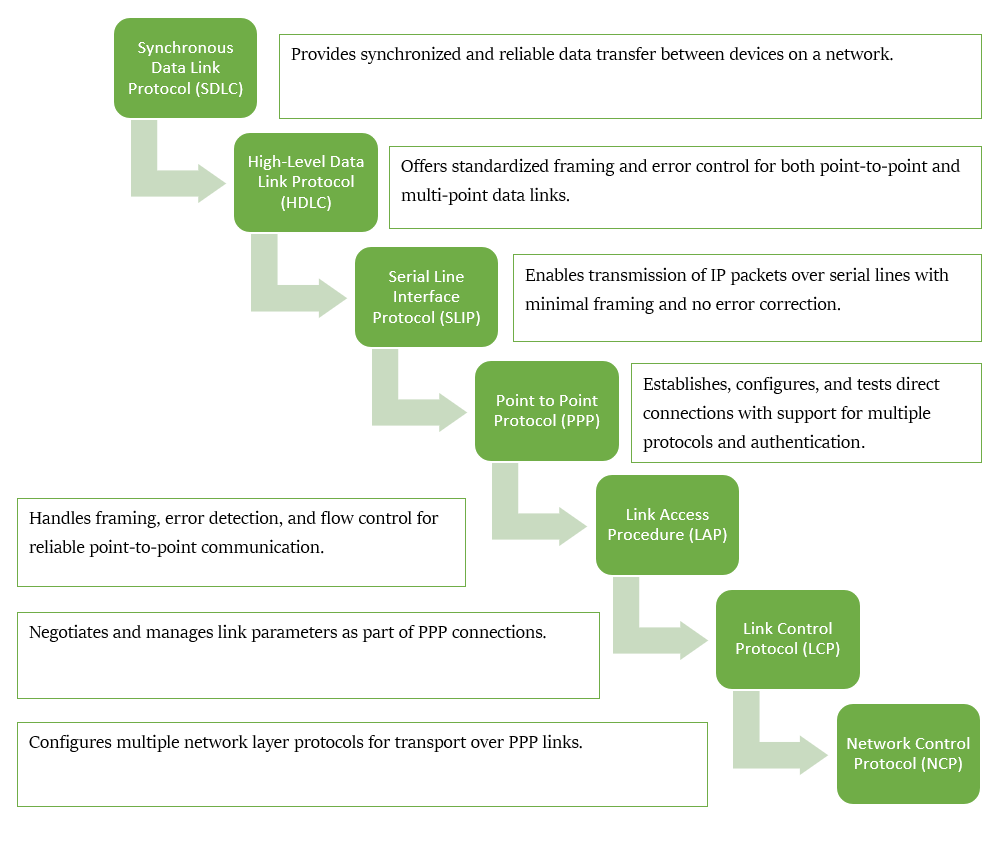
PROTOCOLS OF DATA LINK LAYER
Network Layer
It is the third layer of OSI model that ensures reliable end-to-end packet delivery across multiple interconnected networks.

This layer assigns logical addresses (IP addresses) to devices and encapsulates the transport layer data into packets. Then further the network layer performs routing to select the optimal path for packets to travel through different networks and handles packet forwarding between routers and manages fragmentation and reassembly to accommodate varying network MTUs. It supports subnetting and Network Address Translation (NAT) to improve address management and security
PROTOCOLS OF NETWORK LAYER

Transport Layer
It is the fourth layer of OSI model that ensure end-to end communication between applicartion on different hosts. This layer is placed between Netwok and Session layer that delivers data reliably in correct order.
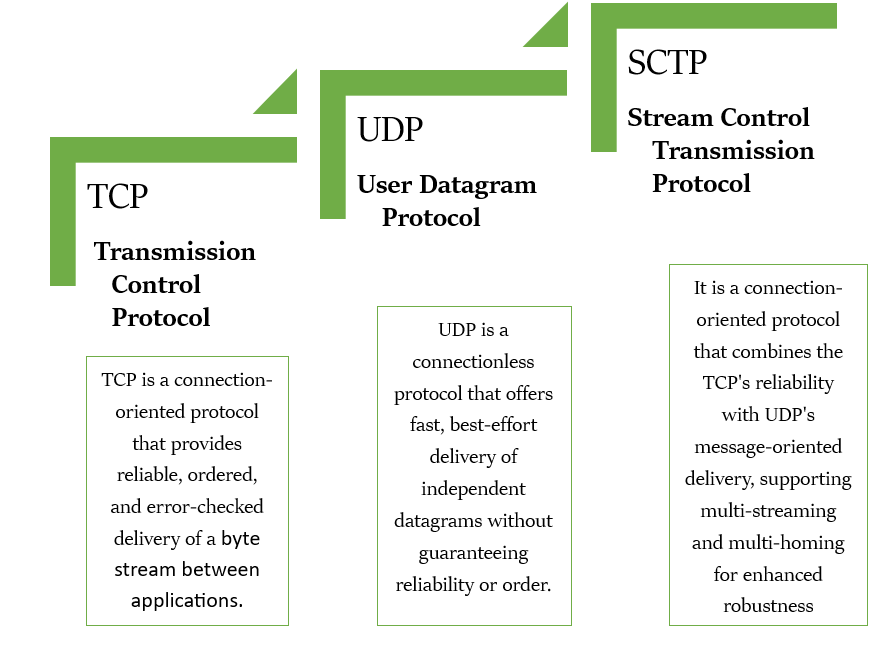
This layer manages process-to-process data delivery using port numbers, ensuring data is transferred in the correct order, error-free, and without loss. Major functions include segmentation of data into smaller units (segments or datagrams), error detection and retransmission, flow control to prevent receiver overload, and multiplexing to support multiple application connections over a single network link. The transport layer uses protocols such as TCP (connection-oriented and reliable) and UDP (connectionless and faster) to suit different communication needs. This layer is implemented on end systems only, not intermediate devices, and plays a critical role in enabling reliable, organized data transfer between applications across networks
PROTOCOLS OF TRANSPORT LAYER
Session Layer
It is the fifth layer of OSI model that establishes, coordinates and terminates smooth data exchange between the application on different devices

This layer provides mechanisms for session setup, dialog control (deciding whose turn it is to send or receive data), synchronization, and recovery from failures during long or complex data exchanges. This layer ensures data streams remain organized and reliable by managing checkpoints and graceful session termination. Although modern networks sometimes handle its functions at the transport or application layer, the session layer plays a crucial role in coordinating semi-permanent dialogues for application processes.
PROTOCOLS OF SESSION LAYER
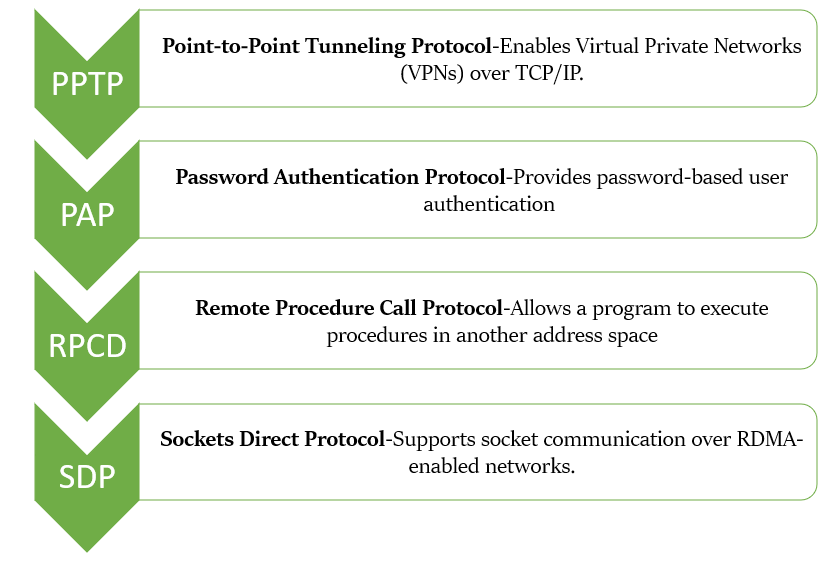
Presentation Layer
It is the sixth layer of OSI model that acts as a translator for the network, ensuring that the data exchanged between devices is in such a format that both systems can understand.

The functions of this layer includes data translation (e.g., character code conversion), data compression to optimize bandwidth, and data encryption and decryption for secure communication. This layer manages syntax and semantics of transmitted data, enabling interoperability between heterogeneous network environments. It works between the application layer and session layer, preparing data for transmission and processing received data into a usable form.
PROTOCOLS OF PRESENTATION LAYER
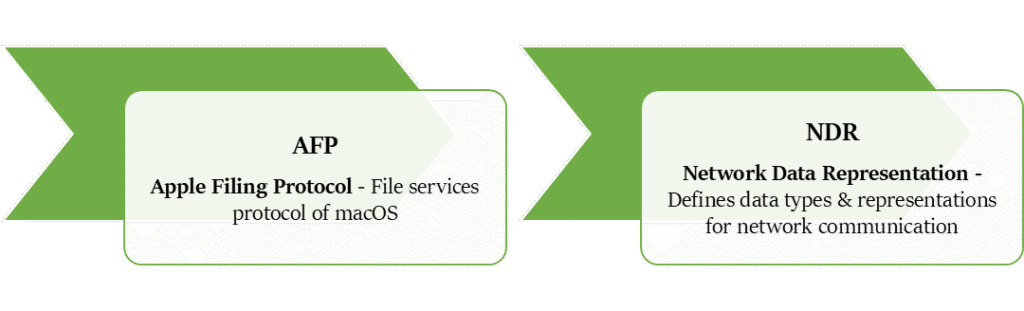
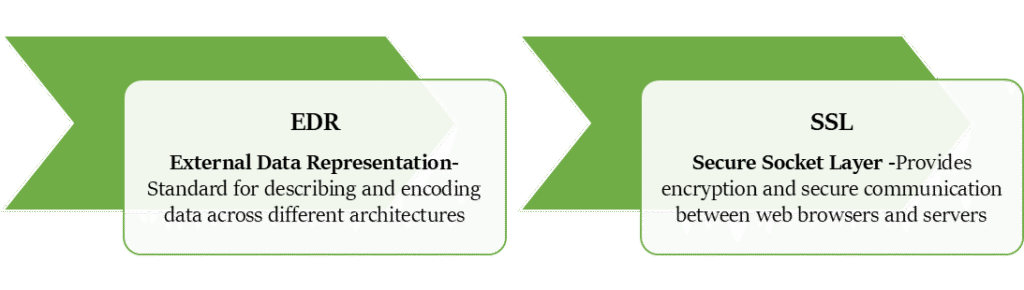

Application Layer
It is the seventh layer of OSI model that acts as an interface between the user and the application.
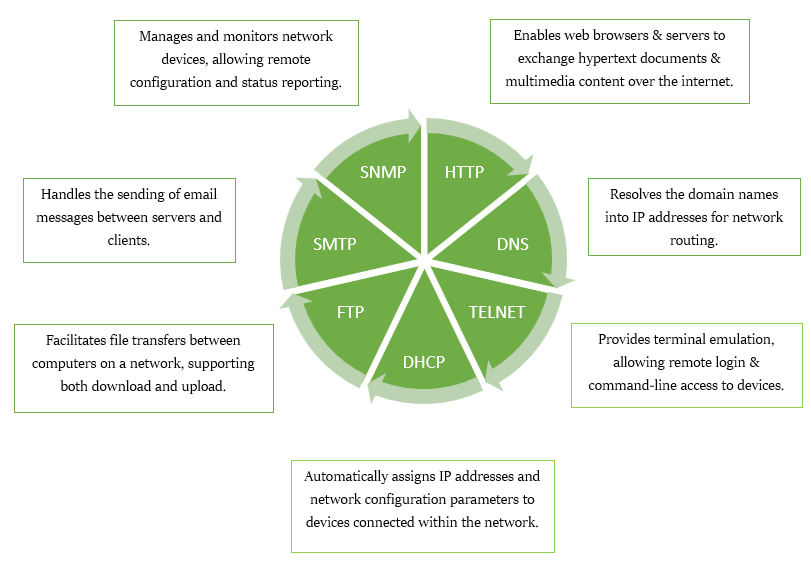
This layer acts as an interface between the user’s software and the underlying network, that enables the functions such as file transfer, email, remote login, and web browsing. The major responsibility of this layer is to represent data in a standardized format, accessing various network services, managing communication sessions, and defining protocols like HTTP, FTP, SMTP, and DNS. This layer ensures that user requests and responses are properly formatted, transmitted, and understood across multiple network systems.
PROTOCOLS OF APPLICATION LAYER
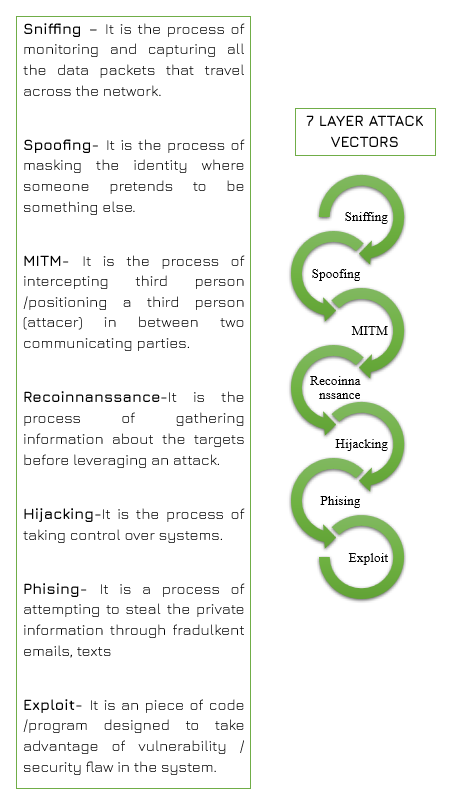
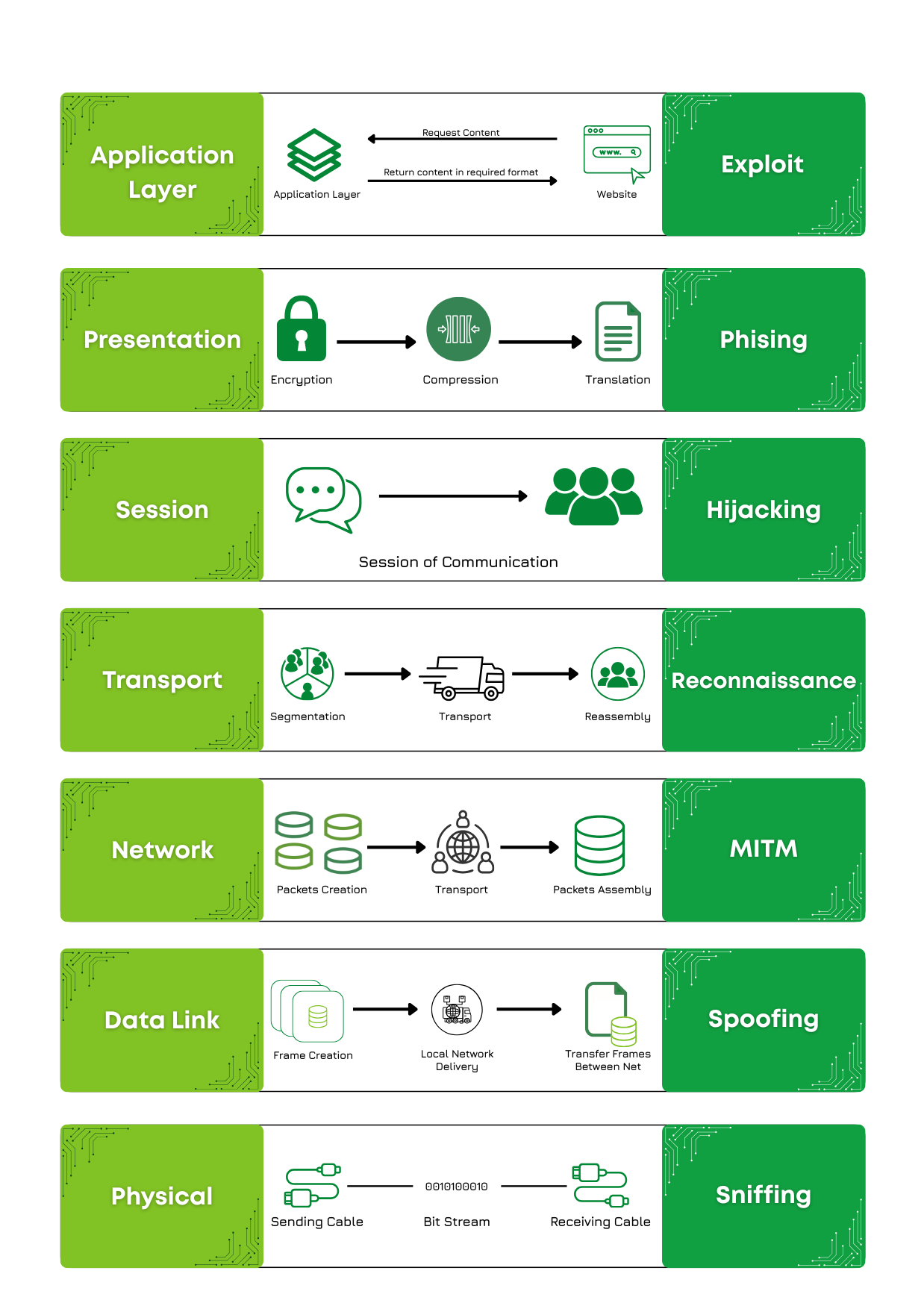
Data Flow and Exploitation Paths in the OSI Model
Imagine an IT company in Nepal is placing an order for network hardware with a supplier based in USA via email. The communication flow through the OSI layers is as follows:
Application Layer (Layer 7)
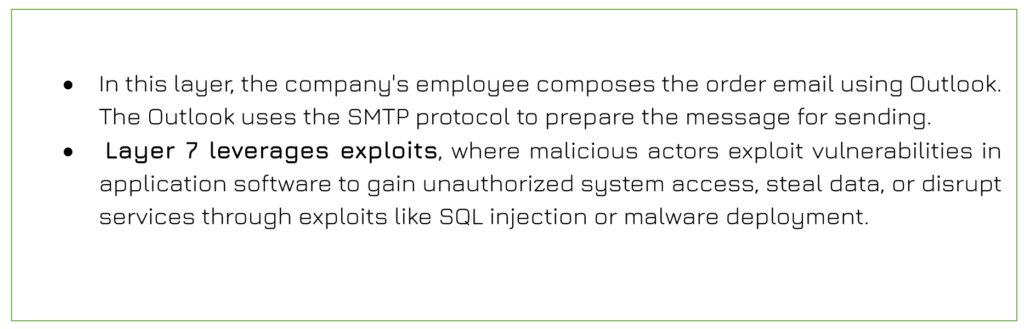
Presentation Layer (Layer 6)
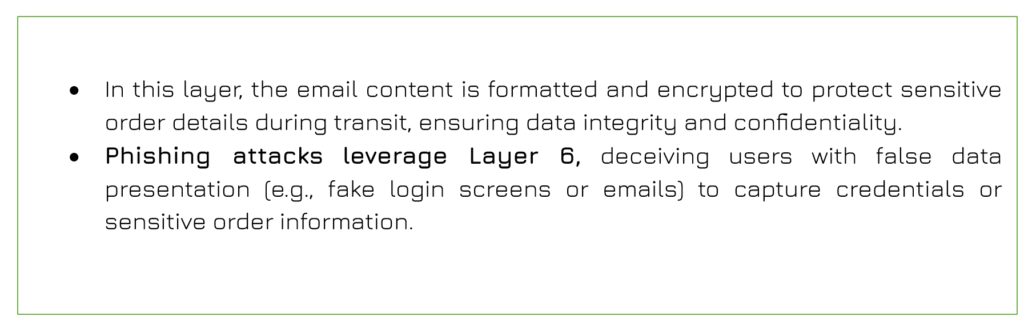
| Session Layer (Layer 5) |

Transport Layer (Layer 4)

Network Layer ( Layer 3)

Data Link Layer ( Layer 2)
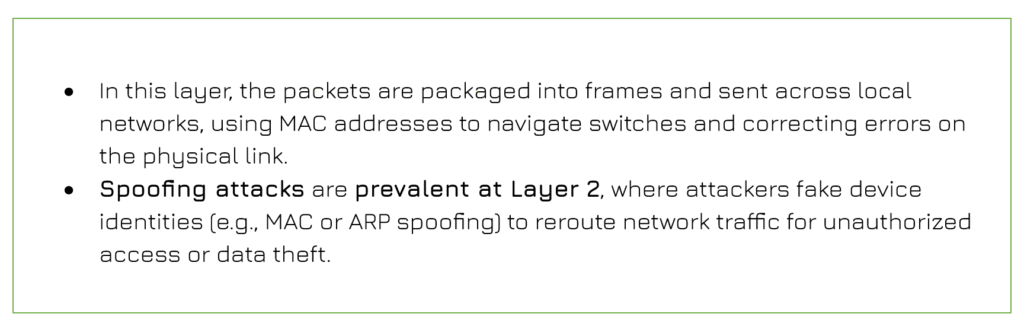
Physical Layer (Layer 1)
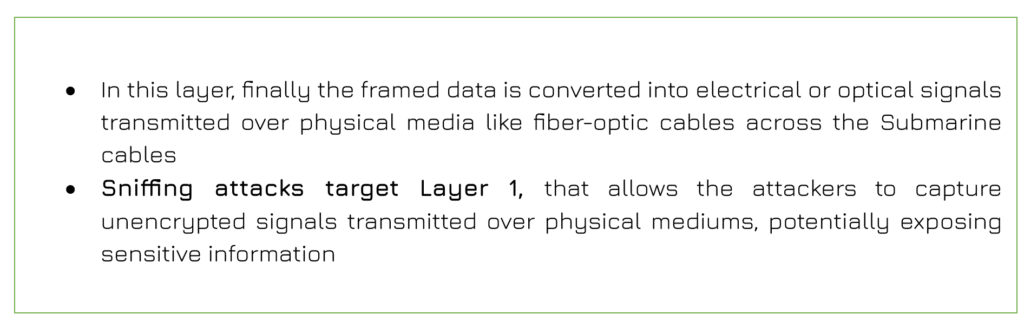
After the email reaches the supplier’s email server in USA, the process reverses, and then the physical signals are converted back into data frames, checked and reassembled upward through the layers until the email appears in the supplier’s inbox for processing the order.
In a nutshell, this article shreads a light upon instant concern of coordinated, defense-in-depth approach of security across the OSI model that recognizes both layer-specific threats and the ways those threats can be eliminated. It also helps the organization to identify secuirty gaps at each layer and pairing them with practical mitigations, the organizations can reduce attack surfaces.

